
What is a VPN?
A Virtual Private Network (VPN) is a technology used to create a secure and encrypted connection to a private network over the Internet.
What is VPN used for?
The use of VPN servers has two primary purposes:
- Remote connection of employees to a private office network or accessing content unavailable in the country of residence. (For example, Netflix may not be accessible in certain regions.)
- Encryption of all your internet traffic data.
VPNs act as primary guardians of security on the internet. You connect to a private Internet network using a VPN instead of the public and unsecured Internet.
A VPN lets you surf the internet anonymously and hide your identity from monitoring by ISPs and malicious third parties.
As a result, by using a VPN, your online activities become untraceable. This means that when connecting to public Wi-Fi in an insecure environment, the probability of tracking your online footsteps to access your browsing history or awareness of your status will be reduced to zero.
How does a VPN work?
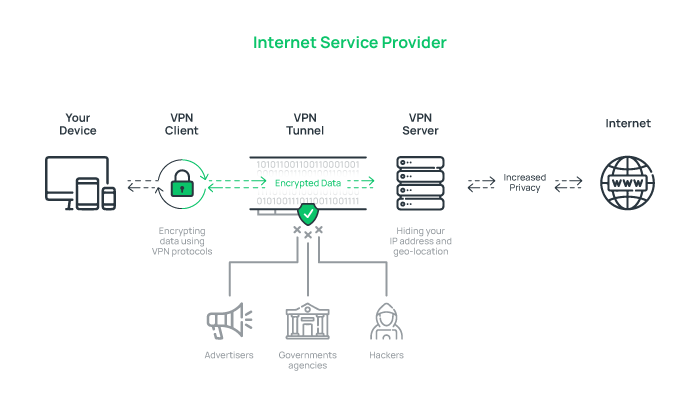
VPN works based on establishing a secure and encrypted connection called a tunnel between the user’s device and the VPN server.
When connected to the internet through a VPN, your internet traffic is transported securely through this virtual tunnel.
VPN secures the connection between the VPN server and the user’s device by creating a tunnel using various protocols and encrypts all transferred data, preventing unauthorized tracking.
Moreover, by replacing the user’s IP address with its server’s IP, the VPN hides the user’s real location and identity and increases privacy while surfing the internet.
Benefits of VPN
• Hides your location and IP address and makes you Anonymous.
• Ensures advanced privacy on public networks.
• Makes tracking of your online activities difficult.
• Protects your personal data through encryption.
• Enhances the security of file-sharing.
• Reduces the risk of unauthorized access to your important data.
• Provides safe remote access to private network resources.
• Assists in bypassing censorship and restrictions.
Disadvantages of VPN
• VPN encryption processes can result in slowing down internet connection speeds.
• In Some Countries, VPNs are illegal; thus, the government may block them to prevent breaking the law.
• Unables to Bypass Cookies and some browser services, allowing online activity tracking by such services.
• Does not provide complete privacy; malicious VPN providers might misuse or sell your data.
• Does not protect against malware or phishing attacks.
• high performing, reliable, and safe VPNs are costly.
Why people don’t use VPN?
People, for various reasons, including concerns about the impact of VPNs on internet speed, worry about compromising their privacy, the high cost of using quality services, and legal considerations in countries where VPNs are restricted, prefer not to use VPNs.
Do I really need a VPN?
VPN is a valuable tool for securing your private data, establishing advanced privacy, and ensuring a secure connection for remote work on the internet. Therefore, you need a VPN to guarantee the security of your online activities.
If you do not use a VPN, your online activities will be traceable and observable by ISPs, other entities, and third parties; the security of your connections will be exposed to cyber threats when you use public Wi-Fi networks. Additionally, Geographic restrictions may also limit your access to certain content and online services.
Types of VPN
VPNs are generally divided into three main categories that account for most of the market:
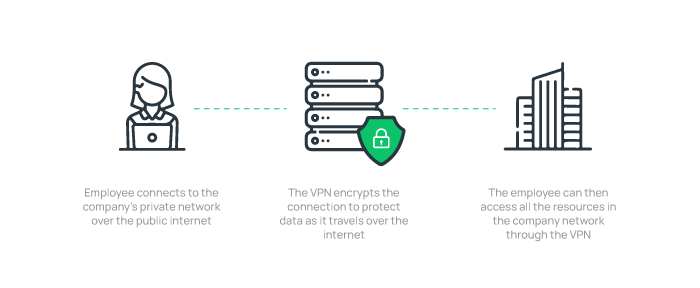
1. Remote Access VPN
Remote Access VPN enables secure remote access to a company’s private network and resources over the Internet for remote employees.
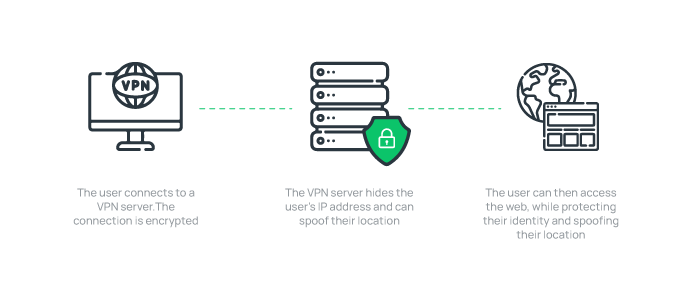
2. Personal VPN
Personal VPN or Consumer VPN is used by the general public to encrypt web connections and ensure privacy while surfing the Internet. Personal VPNs function similarly to remote access VPNs, but personal VPNs connect to your VPN provider’s servers.
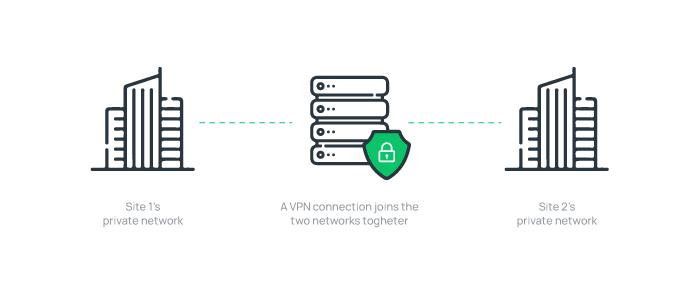
3. Site-to-site VPN
Site-to-site VPNs are typically used by multi-office companies that need secure data transport. Using Site-to-Site VPNs, entire networks are connected over the internet through a secure communication channel, allowing intranets and workplaces to share resources and data securely.
What is a VPN Cisco?
Cisco VPN is a popular VPN solution provided by Cisco Systems, offering secure and encrypted remote access to enterprise networks over the Internet.
Cisco AnyConnect VPN is a valuable tool for safeguarding sensitive data, meeting network security requirements, and improving productivity in enterprise environments.
Different Protocols Of VPN
The VPN protocol specifies the exact path taken by the transmitted data. VPN protocols vary by features, such as data output speed-improving protocols and data packet encryption protocols for privacy and security.
We have examined different VPN protocols with varied security measures before. Here, we will mention some of them:
-
PPTP
Point-to-Point Tunneling, or PPTP Protocol, is a VPN protocol that has been used for a long time and is the oldest VPN protocol.
But PPTP is known as the least secure protocol in the technology world. However, it is still popular thanks to its fast connection for users who don’t need advanced encryption.
Briefly: strong support, fast, but with security issues.
-
L2TP/IPSec
Layer 2 tunnel protocol L2TP/IPSec is usually implemented by integrating with the IPsec security protocol. L2TP protocol creates an unparalleled security experience without breach after launch.
Briefly: popular and fast but easily blocked because it only uses one UDP port.
-
OpenVPN
OpenVPN is the most secure open-source VPN technology because it can quickly detect and fix even the slightest code errors.
This protocol is one of the most frequently used, giving developers complete freedom by releasing free source code.
OpenVPN protocol is becoming more popular because of its invulnerability thanks to AES-256-bit key encryption, RSA 2048-bit authentication, and SHA1 160-bit hashing.
Briefly: open source, high-level encryption, reduced throughput.
-
SSTP
SSTP (Security Socket Tunnelling Protocol) is widely used since it works with all Microsoft Windows versions. SSTP uses 2048-bit SSL/TLS certificates for authentication and 256-bit SSL keys for encryption.
The SSTP protocol’s major drawback is that developers can’t access the underlying code because Microsoft developed it exclusively.
Briefly: strong security, sophisticated blocking and detection, and great support for native and third-party clients.
What is SSL VPN?
SSL VPN (Secure Sockets Layer VPN) is a type of VPN technology that creates a secure and encrypted connection in an insecure public network (Internet) using the SSL/TLS protocol.
SSL VPN is a secure solution for user’s remote access to an organization’s network or private resources via the Internet.
VPS or VPN
A VPS is a virtual server that provides a hosting environment with dedicated resources and high speed. However, a VPN is a network technology that enhances online privacy, offers remote access to company networks, and secures Internet connections.
What is a VPN router?
A VPN router is a router equipped with built-in VPN software.
VPN router allows you to connect all devices simultaneously to the VPN server without needing VPN configurations on each device individually and it provides better performance and stronger security than VPN software on individual devices.
You can ensure your network’s security and privacy with a VPN router. It encrypts all of your devices’ internet data and facilitates the use of VPN at the router level.
Does VPN work on home Wi-Fi?
Yes, a VPN can work on home Wi-Fi by setting up a VPN on your router, enhancing the security of your home network.
How do I set up a VPN at home?
- Choose a reputable VPN provider.
- Install and configure the VPN client for your router through the link provided by the VPN provider.
- Follow the VPN client’s manual instructions specific to your router and your chosen VPN provider for connecting the VPN router to your modem.
- Access your VPN router’s web interface through your router’s IP address and router password.
- Look for VPN in the Settings menu and tap on it.
- Select the VPN client (ensure not to choose the VPN server).
- Enter your VPN provider’s credentials (from your account settings or website).
- Follow the instructions as per your router’s request.
- Save your settings.
What is VPN on iphone?
A VPN on iPhone is a virtual private network service that allows iPhone users to connect to a private network via the mobile network. When VPNs work on iPhones, they provide advanced privacy and security when connecting to public networks By encrypting internet traffic and hiding the user’s IP address.
Do I need a VPN on my phone?
Yes, you need a VPN on your phone because using a VPN on your phone encrypts your internet traffic, protects privacy, secures connections to public networks, particularly while using public Wi-Fi, and ensures anonymous surfing on the Internet.
Is VPN free for iPhone?
Yes, several free VPNs are available for iPhone, which you can use on an unlimited number of devices by using your Apple ID.
However, keep in mind that free VPNs have limitations.
How can I use VPN on my phone for free?
- Download the free VPN app from your device’s app store (for example, Google Play or the App Store).
- Create an Account if needed.
- From the available options, select the server location to connect to the server.
- Tap the “Connect” button to connect to the VPN server and enjoy secure access.
How do I activate VPN on my phone?
On Android:
- Navigate to the “settings” app.
- Find “Connections” or “Network & Internet” and tap on it.
- Select “VPN” or “More connection settings.”
- Tap on “Add VPN” or the “+” icon.
- Enter VPN Details, including VPN type, name, server address, etc.
- Tap “Save” or “Connect.”
On iOS (iPhone):
- Open “settings” from the Home screen.
- Look for “General” and tap on it.
- Tap on “VPN or “Add VPN Configuration.“
- Enter the necessary information, such as server name, account credentials, password, etc.
- Select “Save.”
- Toggle the VPN switch from off to on to connect.
Where is VPN on my Phone?
On most phones, you can find VPN settings in the “Network & internet,” “Connections,” or “Wireless & Networks” category of your phone’s settings menu.
If you haven’t been successful in finding a VPN yet, you can use the search function in the settings menu.
Does Android have a built in VPN?
Yes, Android devices running version 4.0 and later have a built-in VPN feature that supports PPTP, L2TP/IPSec, and IPSec protocols.
Can VPN Slow Down Internet?
Yes, in most cases, using a VPN instead of making the internet faster can lead to a slowdown because a VPN adds an extra security step to encrypt your traffic.
Can VPN help with ping?
Although VPN leads to latency, it can improve ping times in certain cases.
VPNs, in situations such as the proximity of the VPN server to the target server, inefficient ISP routing( VPN can provide a more direct route to the destination server), and ISP throttling (bypassing restrictions by VPN) contribute to reducing ping times.
Can VPN Block Ads?
VPN is intended to encrypt internet connections and provide online privacy; inherently, is does not block ads.
However, some VPNs, like NordVPN, Surfshark, ProtonVPN, etc., support features such as ad-blocking or malware protection.
By masking your IP address, such VPNs free you from websites that track your online activities and offer targeted ads, so they indirectly block ads.
As a result, by blocking websites or ad-serving scripts, these VPNs assist in limiting or removing ads from your surfing experience.
Can VPN bypass IP ban?
Yes, by changing your original IP address to the VPN server’s IP, the VPN can bypass IP bans.
By connecting to a VPN, your internet traffic is routed through VPN servers located in different countries, making it appear that you are accessing a service or website from a different location and IP address.
As a result, a VPN helps bypass IP restrictions by hiding your actual IP address.
Can I watch Netflix with VPN?
Yes, you can watch Netflix using a VPN. You can bypass geographical restrictions on Netflix content by connecting to a VPN server located in a country that allows Netflix content access.
However, it’s worth noting that Netflix is continually identifying and blocking VPN traffic, so not all VPNs may work successfully with Netflix and overcome these restrictions.
Why does Netflix block VPN?
Netflix blocks VPNs to adhere to licensing agreements, as VPNs enable users to bypass geographical restrictions.
Based on licensing agreements, due to legal considerations, Netflix has the right to broadcast specific content in particular regions and access to specific content in some countries is restricted.
Therefore, Netflix is to enforce restrictions to comply with licensing agreements.
What country has the best Netflix?
- Slovakia
- United States
- Japan
The best country for Netflix depends on individual preferences, which vary for each person based on content, language, and pricing.
Slovakia has claimed the top spot in the list of the best countries for Netflix, considering its wide range of available content and cost-effectiveness.
Can VPN hide my location?
Yes, a VPN hides your real location by masking your actual IP address to preserve privacy.
The VPN server acts as an intermediary, receiving your internet traffic and directing it towards the destination. As a result, your IP address appears as the VPN server’s IP address when browsing the internet.
This challenges determining your real geographical location for websites, online services, and other entities.
Can VPN be hacked?
No technology can be considered entirely secure. If a VPN is not configured properly and does not provide a high level of protection and security, it may be vulnerable to hacking and other potential threats.
Reasons such as weak encryption in VPNs, improper configuration of VPN clients, server infrastructure vulnerabilities, logging policies and the recording of user online behavior, DNS leaks, etc., can compromise the security of your system against cyber criminals.
Should VPN be on or off?
It depends on your situation and requirements.
Leaving on the VPN all the time protects your device and data from cyber-attacks, especially when using public Wi-Fi, protects your privacy, and ensures a secure connection to the internet. It also makes it difficult for third parties to monitor your online behavior.
However, in certain situations where you don’t prioritize security, such as online gaming or video streaming, where a VPN may lead to a decrease in internet connection speed, or when some services are incompatible with the VPN, you can turn off the VPN.
Do VPNs cost money?
Regarding cost, there are two main categories: free and paid.
Although free VPNs are available in the market, popular and high-performance VPNs cost money and vary in price.
Is free VPN better than paid ?
Paid VPNs offer higher speed, increased security, and better overall performance than free VPNs.
Free VPNs come with limitations and are generally weaker regarding privacy and security.
Is there a 100% free VPN?
Yes, 100% free VPN services are available on the market, including ProtonVPN, Windscribe, Hotspot Shield, PrivadoVPN, TunnelBear, etc.
Are VPNs safe?
VPNs are designed to enhance your online privacy and security, but they cannot protect you against malware, viruses, cookie tracking, and phishing scams.
They also cannot guarantee 100% protection against data leaks. This is especially true for free VPNs or malicious VPN service providers that may compromise your data and system security by logging your activities.
VPN security depends on the provider’s credibility, so choose cautiously.
Do I need a VPN for online banking?
Using a VPN for online banking is not necessary, but it is useful for ensuring an additional layer of security, encrypting your connection to the bank, and enhancing privacy during online financial transactions.
Although online banking platforms currently utilize strong security measures and encryption protocols to protect your information, using a VPN while online banking on public Wi-Fi networks is a precaution.
It should be mentioned that there is no room to worry about using a VPN when banking online because it is entirely safe.
Why do banks block VPN?
Banks typically block VPNs to prevent fraud and unauthorized access and enhance security.
Banks express concerns about potential fraudulent activities, and since identifying the true origin of a connection has become challenging for banks, the use of VPNs is marked as suspicious behavior.
Banks assume that individuals hiding their real location and identity through VPNs may be involved in fraudulent activities and malicious actions.
Can banks see your IP address?
Yes, banks can see your IP address during online banking for the purpose of User Authentication verification, security monitoring, and identifying suspicious activities.
Can a VPN be traced?
VPNs prevent tracking of your online behavior by encrypting your internet traffic and revealing just the VPN server’s IP address.
However, no technology guarantees complete anonymity; there is a risk of exposing your online activities when the VPN service provider logs your online activities, the VPN is susceptible to DNS, WebRTC, or IP address leaks, or your device becomes infected with malware.
Can Google track me if I use VPN?
Yes, Google can track you even if you use a VPN through methods such as cookies, device fingerprinting, and Google Analytics, and it can be aware of your location.
However, the level of tracking is limited, and collecting information about your IP address and ISP is challenging.
You can challenge Google’s online tracking by using tricks such as blocking Google Analytics with browser extensions, using browsers that prioritize your privacy (such as the Tor Browser), and clearing or blocking cookies.
Can the police track a VPN?
In specific circumstances, tracking your activities may be possible for the police but not always easy.
VPNs protect user privacy by encrypting traffic, but they are not foolproof.
On the other hand, In cases where law enforcement is determined to trace a user, they can collaborate with the VPN provider or Internet Service Provider (ISP) to obtain a report of the user’s online activities through a court order.
Can a VPN see your searches?
Yes, a VPN service can potentially monitor your browsing history and online activities.
However, by choosing a reputable VPN provider, you can ensure that your browsing history will not be logged, and you can prevent potential eavesdropping by third parties.
Do VPNs sell data?
Your response varies depending on the VPN provider; reputable providers that adhere to privacy policies, including a strict no-logs policy, do not sell user data.
According to the Privacy Policy of a trustworthy VPN provider, they are not allowed to log your online activities, and as a result, they cannot sell your data to third parties or advertisers. However, this risk exists with free VPNs.
What is the best free VPN?
• ProtonVPN: Strong privacy and security features.
• Windscribe: Generous free plan, ideal for bypassing geographical restrictions with a wide range of server locations.
• TunnelBear: Best for hiding your VPN traffic from your ISP and ease of use.
• Hide.me: Privacy protection even in VPN disconnection and security against leaks.
• Hotspot Shield Free: Suitable for blocking internal ads and protecting against malware.
• VPN Unlimited: Good for protecting online privacy.
What should be considered when choosing a VPN?
-
Security and privacy
Advanced privacy and data security are most VPN users’ priorities. Ensure the VPN service uses strong encryption protocols such as OpenVPN and advanced encryption standards.
Ensure your VPN provider’s strong no-logs policy respects your privacy and prevents data from being recorded.
-
Speed and performance
Secure connections and data protection require speed sacrifices. Since VPNs add encryption and security layers to internet connections, speed may decrease.
However, the quality of the VPN server infrastructure, server bandwidth, traffic on the VPN server, distance to the VPN server, VPN server capacity, and performance affect VPN connection speed.
Therefore, you can choose a VPN provider that does its best to improve VPN performance.
-
Cost
While free VPNs have always attracted customers, they will not meet your expectations regarding data security, privacy, and speed, as they rarely invest in optimizing the infrastructure of their services.
Free VPNs often use weak security protocols like PPTP and fewer servers to cover bandwidth, resulting in unstable connections and compromising privacy.
Also, Some providers make money from selling user data, and Some free VPNs limit uploads and downloads.
Therefore, choose a reliable VPN provider over a cheap one since you use a VPN to secure connections and maintain privacy, not to risk your vital data.
As a result, Finding the most reliable and fast VPN service providers requires research. Be strict in choosing the best VPN provider. Ensure you won’t find the right service for free.
What VPN should I use?
Choosing a VPN for use depends on your specific needs. Despite the wide variety of VPN services on the market, ExpressVPN, CyberGhost, NordVPN, Surfshark, and Proton VPN are good VPN services and have often received positive reviews.
Is Google’s VPN any good?
Google’s VPN service, known as Google One VPN, is one of the reliable VPNs that provides a satisfactory level of security and privacy through strong traffic encryption and a no-logs policy.
Since Google is a data-driven company, it cannot be considered one of the most secure solutions for not monitoring your online activities against itself.
How do I connect to VPN?
Steps to use VPN for beginners:
- Choose reputable VPN providers and sign up for a subscription.
- Download and install the VPN client on your device.
- Launch the VPN client.
- Log in using your username and password.
- Choose a VPN server location from the VPN service’s list to route your internet connection through that location.
- Connect to the selected VPN server by clicking “Connect.”
Your client interface should show a VPN connection notification or icon after connecting.
Note: Use a VPN server in another country to bypass geographical restrictions. Also, the VPN server’s closeness to your location improves performance and speed.
How do VPNs make money?
VPN providers make money by charging subscription fees for users to access their VPN services, partnering with some affiliated companies (through in-app advertising or affiliate marketing), and integrating their services with third-party products.
Additionally, some VPNs profit by collecting and selling anonymized user behavior data to third parties for analytical and marketing purposes.
Offering premium features with additional costs and providing paid support services are other ways VPN providers can make money.
What is the easiest way to set up a VPN?
Buy a reliable VPN service and set it up using the information provided by the VPN provider(such as server address and account credentials) and pre-configured protocols on your device (such as IKEv2/IPsec, L2TP/IPsec, PPTP, and SSTP).
FAQ
What are the benefits of VPN?
- Hiding the identity, real IP address of your system, user's online activity, and user's personal data on any network
- Protect your important data from hackers and spies on public networks with encryption
- Bypassing restrictions on access to some content
Does VPN hide all online activities?
When you connect to a VPN, your IP address changes, but your online activities will still be visible to every site you have an account on. Your images, posts, and shares are still accessible to everyone. VPNs can help you feel more secure in your online activities but cannot prevent cyber attacks.
Conclusion
Using a VPN in an insecure internet environment has become a necessity. If you cannot trust VPN providers and connecting to various locations is not crucial, we recommend configuring your own VPN server by purchasing a VPS.
This article has explained the VPN’s function and its pros and cons, and you now know that you need a VPN compatible with your goals to secure your online activities. So do not hesitate to use VPNs; security is one of the most critical issues.