
How To Detect And Prevent DDoS Attacks?
DDoS attacks are usually among the attacks that can be predicted and prevented. To do this, you can block attackers from accessing your website through the methods we describe in this post. And increase your site’s security more than before so that you can provide services related to your website to your users more efficiently and faster than before.
What Is A DDoS Attack?
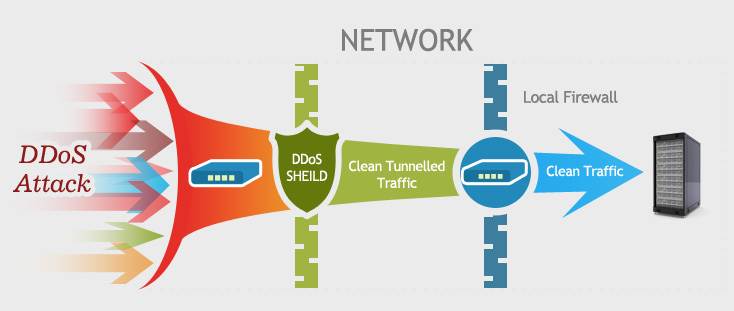
DDoS attack stands for Distributed Denial Of Service in simple terms, meaning that many requests flow to a server and overuse resources (CPU usage, database, bandwidth, memory, etc.). Through this process, service regularly disrupts it or becomes inaccessible to users.
Due to the high volume of processing or the so-called overload of server operations, in this type of attack, once or for a while, the attacker will attack you through various computers that may have been used intentionally or even unintentionally, a server (with specified IP) requests information, sends and makes the server inaccessible.
DDoS Attacks Are Divided Into Different Categories
- ICMP flood
- Denial-of-Service Level
- Unintentional denial of service
- SYN
- Teardrop attacks
- Reflected / Spoofed attack
- Low-rate Denial-of-Service attacks
- Distributed attack
- Peer-to-peer attacks
- R-U-Dead-Yet?
- Asymmetry of resource utilization in starvation attacks
- Nuke
- Permanent denial-of-service attacks
- Application-level floods
Note: Most of these attacks resolve automatically with Cloudflare or other CDN’s help, but some of these attacks are more serious, which we will explain.
ICMP Flood
This method disrupts the server by sending ping requests to the person in question. Sending large volumes of ICMP requests to a network will not be available to all hosts on that network.
Assume that any host who responds to this request redirects a large amount of response to the network’s access point and causes the switch to fail. As a result, the website will eventually become inaccessible.
It is best to respond to the ping command to disable all network hosts and prevent suspicious packets from being transmitted within the network. It is possible to be done through a firewall named CSF.
R-U-Dead-Yet? Attacks
This attack is carried out using sessions that are waiting for web applications to be requested. To prevent these attacks, first, the use of up-to-date operating systems is significant because the tool used for web-based DOS requires an element to enter information such as a username field. If the first page lacks an input form, its first page will be protected from attack.
SYN Flood Attacks
In this attack, the three-step process of establishing a TCP connection by the part-time attacker is eliminated, leaving the server waiting for the rest of the steps. When the number of requests is high, the server will no longer communicate with new offers; therefore, the server becomes out of reach.
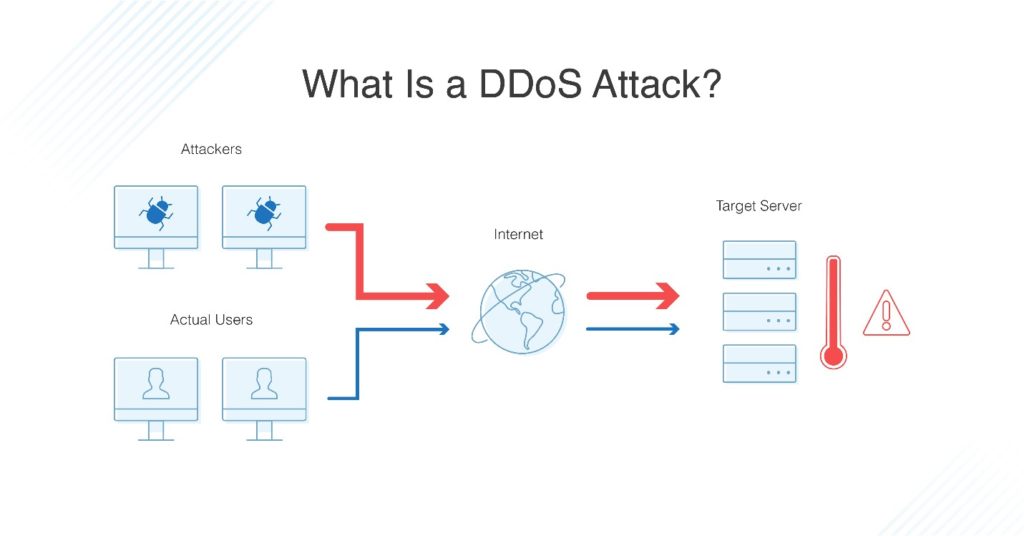
What Is The Difference Between DOS And DDoS?
In both cases, the victim server remains attacking, but the difference is in the attack type. In a DOS attack, an attacker runs the program on one PC. In contrast, in a DDoS attack, an attacker uses multiple systems or virtualization systems on the network to infect the target(s).
DOS Attacks With A Variety Of Methods
DOS Attacks At The Network Equipment Level
In this type of attack, software vulnerabilities in hardware operating systems are used to damage or disrupt hardware. For example, in the old router series, one company had a buffer over follow error.
In this case, if you clicked on that phrase and then typed a long phrase in the password field, the operating system and router service would be unavailable.
Attacks At The Operating System Level
In operating system attacks, operational system protocols are used to disable the service. An example of a DoS attack for this type of attack is a death ping attack that uses the operating system’s ICMP protocol. Greater demands are usually applied to the victim system. These types of attacks usually damage the victim’s system.
Attacks In Applications
In this attack, the malicious user creates an endless routine for software running on the victim system. This constant routine causes all available system resources to be used and the victim system to become inaccessible. So make sure the software you run or download does not carry viruses or malware.
How Can You Prevent DDoS Attacks On Linux?
DDoS attacks on Linux disrupt the web server, and because a web server like Apache is weak against DDoS attacks, It causes content and files to load very slowly.
In these cases, you can see the list of IPs connected to the server and the number of connections on Linux servers using the following command:
netstat -atun | awk ‘{print $ 5}’ | cut -d: -f1 | sed -e ‘/ ^ $ / d’ | sort | Uniq -c | sort –n
Log in to your CSF confiding and precise PORT 80 from the TCP_IN TCP_OUT list.
Note: By doing this, you block port 80 on your server, and you can safely go to the next step. You can do this if you do not want the websites to be out of reach.
After closing PORT 80, first, enter the Firewall Config System and make the following changes.
Set the settings for the CSF.conf file as follows:
DOS and SYN flood protection
- CT_LIMIT = “80”
- CT_INTERVAL = “50”
- CT_PERMANENT = “1”
- CT_BLOCK_TIME = “1800”
- CT_INTERVAL = “60”
- CT_SKIP_TIME_WAIT = “1”
- SYNFLOOD = “1.”
Now your server is protected from DOS and SYN attacks, and you will be notified by email when an IP is blocked
- connlimit = “22;5,80;20”
The number of simultaneous connections allowed for port 22 is five and for port 80 is 20
- PORTFLOOD = “80;TCP;20;300”
This setting means that all requests to port 80 of TCP type from 20 requests per second Limit to 300 seconds before the connection is released.
You can set LFD to detect suspicious directories:
- LF_DIRWATCH = “300.”
When you enter the following command, your server will display a list of IPs connected to your server + the number of connections.
- netstat -atun | awk ‘{print $5}’ | cut -d: -f1 | sed -e ‘/^$/d’ |sort | Uniq -c | sort -n
Enter the displayed IPs in the iplocation website to find the location of the IPs.
And after displaying the details in the Country Code section, you will find from which country you are under attack.
whatismyISP site helps you to obtain information about the ISP of the attacker for research purposes.
Note: Get all the IPs displayed first, enter Config Server Firewall like the above tutorial, place them in the CC_DENY list, restart the CSF and LFD service, and then reboot your server. And then open port 80 on your server.
Note: This tutorial is for attacks on level 7 of the network (software level) that have attacked the web servers. In attacks on the web, etc., You can’t stop attacks from any software other than a hardware firewall.
Easiest Ways To Prevent DDoS Attacks In Windows 10
After you buy Windows VPS or RDP, you may face attack(s) t your server, to prevent this, the Windows firewall has some tools.
Windows Firewall allows the user to create rules and control incoming and outgoing traffic. To learn how to create rules in the Windows server to increase security against DDOS attacks, pay attention to the following:
- Click Server Manager in the Task Bar.
- Go to the Tools menu and click on Group Policy Management.
- On the Advanced Security tab, click Windows Firewall.
- On the next page, you will see the Inbound Rules option.
- Click on the “Action” option to create new rules.
- A new window will open that includes options such as Program, Port, Predefined, and Custom.
- You can create the rules you need according to your wishes.
Note: If you have a remote connection to your Windows server or RDP, you can also use the below link.
Protect RDP Against Brute-Force Attacks
Summary
If you’re pretty sure you are under DDoS or DOS attack, it’s best to contact a professional in the field.
1- If you can’t access your files or other websites from your computer, contact your network administrator.
2- If you have such conditions on your home computer, contact your ISP.
3- You can block it if you find a specific IP. You may have to stop an IP range. (Server administrators have access to these settings).