How to Block Port Scanner and Prevent It in Mikrotik
Is your privacy your no 1 concern? You need to prevent your Mikrotik from being scanned by some websites or apps. They obtain thorough reports on the active ports. Block Port Scanner in Mikrotik is the solution to detect and block attackers’ IPs, join us with this visual tutorial to review all the required steps for preventing port scanning in Mikrotik.
On public networks, there are numerous different dangers, including information and identity theft, data loss and manipulation, and service disruption. There are numerous steps that can be made from the networking side to prevent this. One method is to disable the Port Scanner application’s traffic. You can get information about legitimate ways to connect to a network through the port scanner utility after buying Mikrotik VPS to cover your networking purposes. To increase network security and decrease vulnerabilities, scan your network for open ports and decide whether those ports need to be blocked.
What is MikroTik Brute Force and How to Prevent Port Scanner Attacks
Network administrators or Network engineers must prevent security threats to minimize risks and losses of any kind brought on by careless parties. One of the things that should be observed when a device is linked to the (public) internet network is security. On Mikrotik operating systems, attackers try to read the reports of the ports in use. To not let them gain your sensitive data, you must try to find their IPs and block them by adding precise rules that would prohibit dangerous connections.
Previously, you learned How to Block A Port In MikroTik Winbox. SSH, Telnet, and Winbox ports will no longer be subject to future port scans thanks to the creation of dynamic address lists for each pertinent port and protocol.
For each of the SSH, telnet, and Winbox rules independently, brute force attacks are stopped by going through four different Stages with one Jump rule, Level1, Level2, Level3 Tracking list step, and Black List rule, which regulates the frequency of connection requests. In this way, the structure is set up to allow wrong requests to be sent to incoming connection requests a maximum of three times. However, after three unsuccessful tries, the source of the request is prohibited by adding it to the blacklist in a way that blocks it for 30 days.
Port Scanner Blocking Rules
Configuring the below rule allows you to drop the port scanner in Mikrotik.
/ ip firewall address-list
add list = "Black List (Port Scanner WAN)" comment = "Black List (Port Scanner WAN)"
/ ip firewall filter
Add action = drop chain = input in-interface = WAN comment = "(Port Scanner WAN) Block everyone in the Black List." log-yes-log-prefix = "KL_ (Port Scanner WAN) Black List" src-address-list = "(Port Scanner WAN) Black List"
add action = drop chain = forward in-interface = WAN comment = "(Port Scanner WAN) Block everyone in the Black List." log-yes-log-prefix = "KL_ (Port Scanner WAN) Black List" src-address-list = "(Port Scanner WAN) Black List"
add-in-interface = WAN action = add-src-to-address-list address-list = "Black List (Port Scanner WAN)" address-list-timeout = 4w2d chain = input comment = "IP addresses that scan TCP ports Scanner WAN) Adds to Blacklist and blocks for 30 days "log = yes log-prefix =" (Port Scanner WAN) is added to Blacklist "protocol = tcp psd = 21.3s, 3.1Now that you have become familiar with the subject of this guide, stay with us on this guide to find out the best and quickest way to Block Port Scanner in Mikrotik.
Visual Guide to Block Port Scanner in Mikrotik
Let’s go through this guide and learn How to Block Port Scanner and Prevent It in Mikrotik. Follow all the below steps to prevent port scanning on your Mikrotik.
Step 1. Detecting Types of Scans Connections
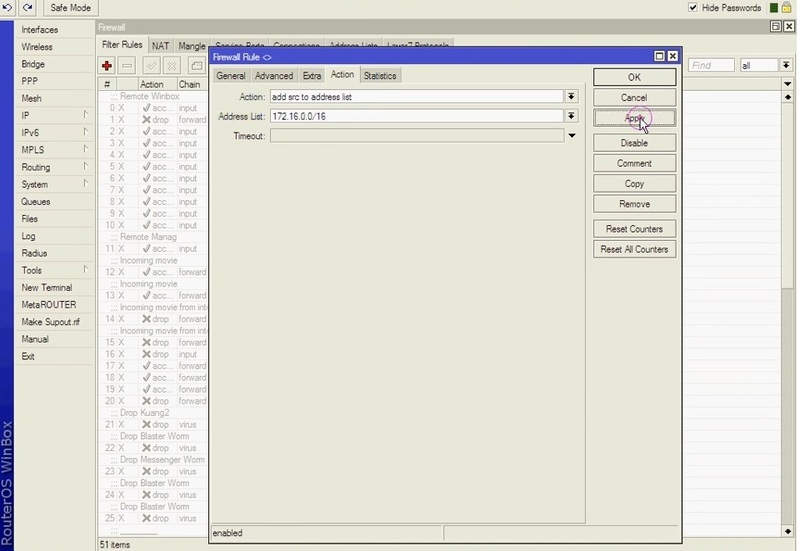
As the first action, you are recommended to find the kind of connections that are utilized for scanning. In order to do this, implement a rule to detect the IPs. Click “+” on the “filter rules” tab after opening IP > Firewall. Choose chain as “input” in the newly opened box, then choose “6(TCP)” for the protocol type. Go to the action tab and choose the “add src to address list” action option. After that, type a name into the address list field or choose from the options.
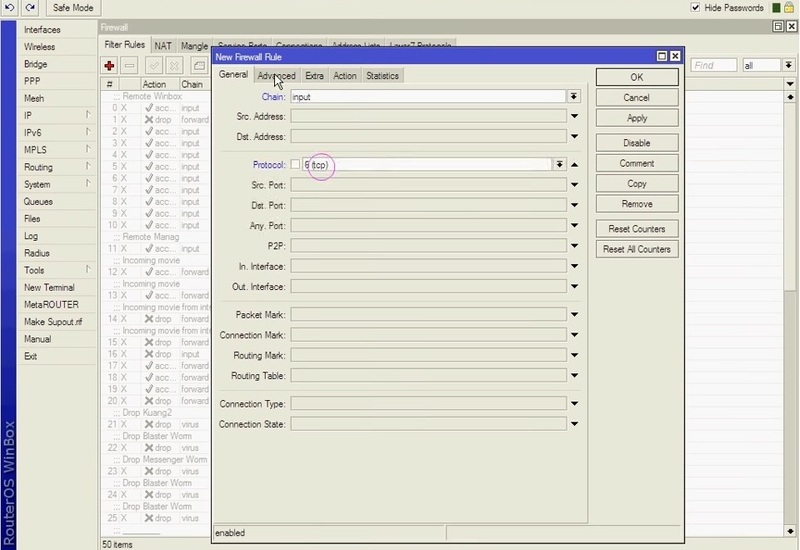
***
Step 2. Remove all the Detected IPs
The step above taught us how to add IP addresses and port scanners to the list. We should remove all of these IP addresses at this stage. In the filter rules tab, click on the “+” symbol after selecting IP>firewall to complete this activity. Click the Advanced tab after selecting chain as the input. Choose your IP list name from the “Src. Address List” and then, when you go to the action page, click the drop-down arrow next to action to select it as a drop.
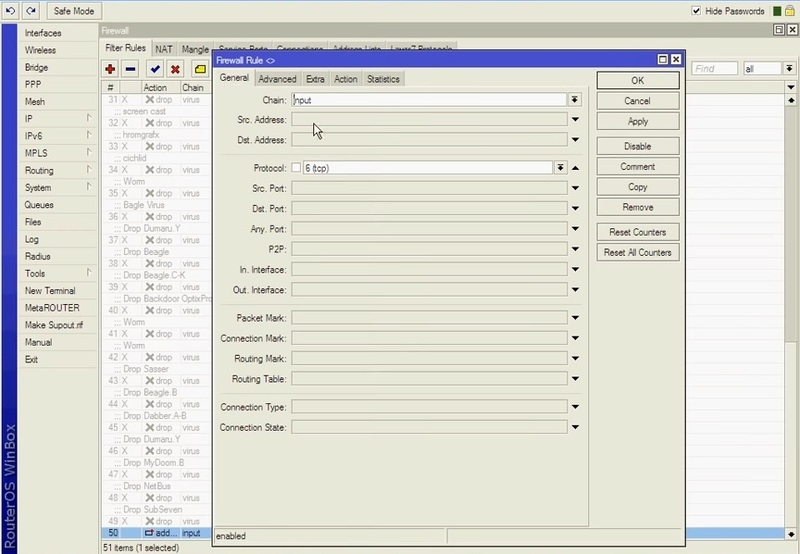
***
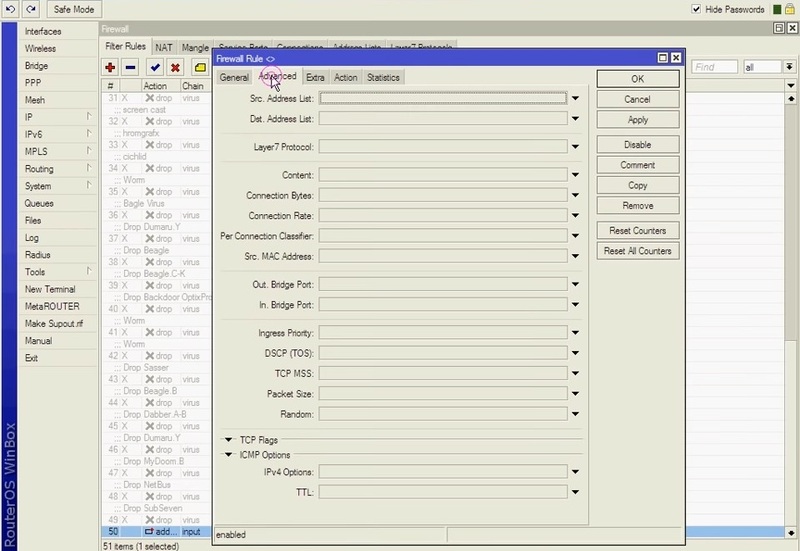
***
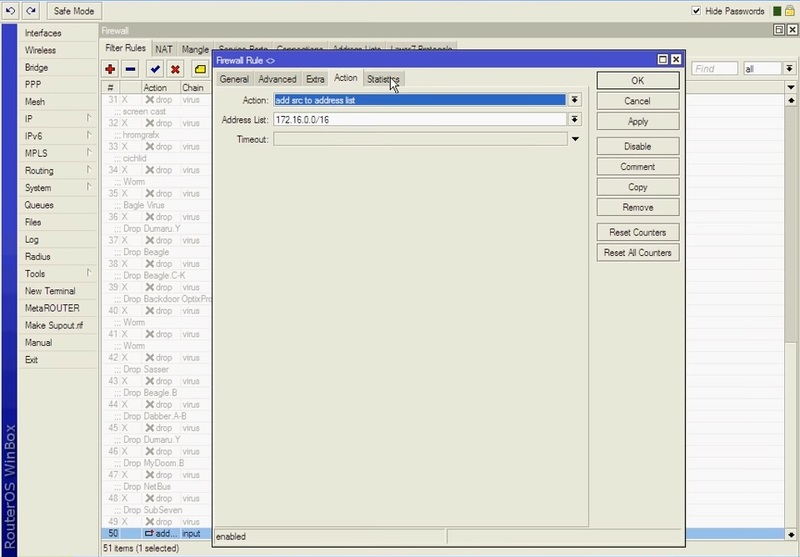
Block scan port Mikrotik was explained in two steps. Let’s learn how to protect Mikrotik after blocking Port Scanner.
What to Do After Find & Block Port Scanner in Mikrotik
So far, you learned how to detect the type of connections used for scanning to block their IPs. As you reviewed it was not that complicated to Block Port Scanner in Mikrotik. But, you are advised when you are sure of getting rid of all the found attackers, protect your Mikrotik server from new Port Scan and IP Address Scans.
Network searches are prohibited by the Firebox’s default settings. The maximum number of allowed address or port searches per second for each source IP address is changeable in this feature’s settings (the default is 10).
You can reduce the threshold for the maximum permitted number of address or port scans per second to more rapidly stop intruders. If you lower it too much, the Firebox can mistakenly classify normal network activity as an attack and block it. The Firebox must send TCP reset packets for each connection it drops, but using a bigger number reduces the likelihood that you may block legitimate network traffic. By doing this, you consume up bandwidth and Firebox resources while also giving the intruder knowledge of your firewall.
FAQ
How can i notice about port scanning on my system?
If the port is open and listening, the handshake contains a RST message that resets the TCP connection and removes the connection attempt from the destination server's logs. Most contemporary intrusion detection systems are capable of detecting SYN port scanning, also known as half-open TCP scanning.
can i sue the port scanners?
While port scanning is not explicitly illegal, yes. Attackers who scan ports and vulnerabilities without authorization risk getting into trouble. You as the owner of the scanned system can sue the person who performed the scan.
Is port scanning illegal?
Unless someone can demonstrate that port scanning was done with the aim to violate privacy or gain unauthorized access, it is not criminal to engage in it. It is typically applied to strengthen security and protect websites.
Conclusion
In this article, you learned How to Block Port Scanner in Mikrotik. The port scan is not a nefarious process in and of itself, but it can guide cyber attackers to obtain your important information. The Port Scan can reveal to an attacker any systems or network vulnerabilities that they can use to break into your company’s network and get access. This quick guide helps you learn what you need to do against attackers to protect your Mikrotik.
If you follow the above steps properly then you can smoothly Block Port Scanner and Prevent It in Mikrotik successfully but do not hesitate to contact us if you encounter any problems. Our technical support team will try their best to solve your problems.