How To Protect RDP From Brute-Force Attacks with RDPGuard?
Brute Force is one of the most common attacks to gain access to RDP login details. As a result, the hacker uses this method to check all possible phrases to get access.
Hackers always try to hack RDPs, and there are some logical reasons for this. The most important reason is that most of the RDP users don’t secure their RDP connections.
But as you know, prevention is better than treatment. As a result, it is better to block the IP which tries to log in to your RDP repeatedly. So, how should You do this exactly??

Stop Brute-Force Attack To RDP With RdpGuard
In this article, we will check how to block suspicious IPs through RdpGuard software. Using the Windows firewall and system event log, RdpGuard diagnoses suspicious IPs and block them immediately. In the setting of this software, you will be able to define to protect which ports and services.
The name of this software starts with RDP, but the software actually ends with 10 other services you can protect.
Protected Services Against Bruteforce Attacks
- RDP
- FTP
- IMAP
- POP3
- MySQL
- MS-SQL
- VoIP/SIP
- WebForms
- RD Web Access
Steps To Protect Your RDP Against Brute-Force Using RdpGuard
- Download RdpGuard.
- Start and complete the installation process.
- Run the software and check any service that you wish to protect.

Step 1: Download RdpGuard from its website.
You should download it from the RdpGuard website.
Step 2: Install RdpGuard On Windows VPS.
- After running the downloaded file, choose Next to start the process.
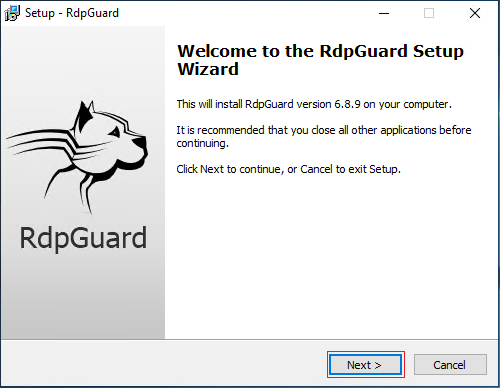
- Check the “I accept the agreement” and choose Next.
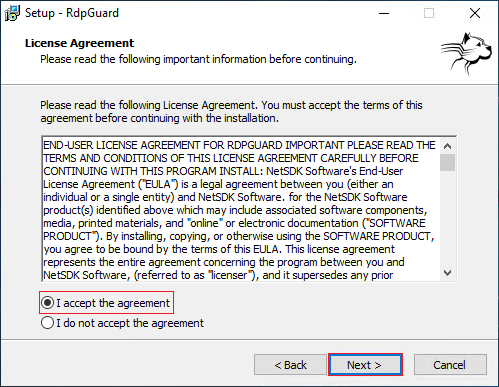
- Select the setup destination location, or you can put it at the default value and choose Next.
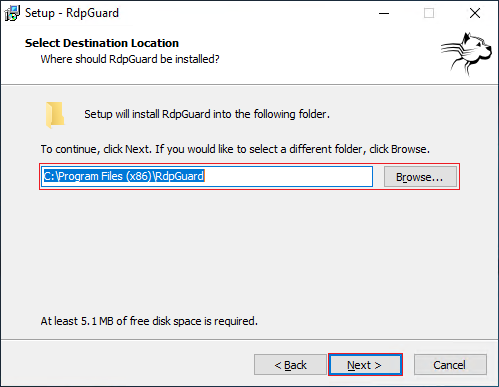
- In the next section, you will be asked if you want to create a desktop icon or not and if you want it for just the current user or all users.
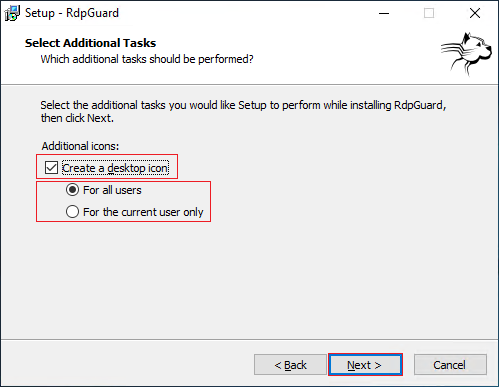
- Congratulations! the installation has been finished. Now check the “Start RdpGuard now” and select Finish.
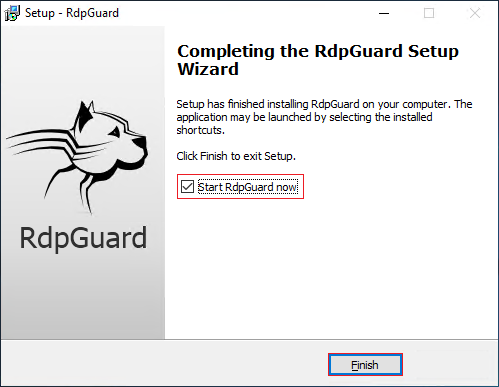
Step 3: RdpGuard Configurations And Setting.
Once the software was opened, you will see that protection for RDP service is activated by default. As a result, you don’t need to make any changes to this one.
And as you can see, some minutes after installing, it has blocked some IPs.
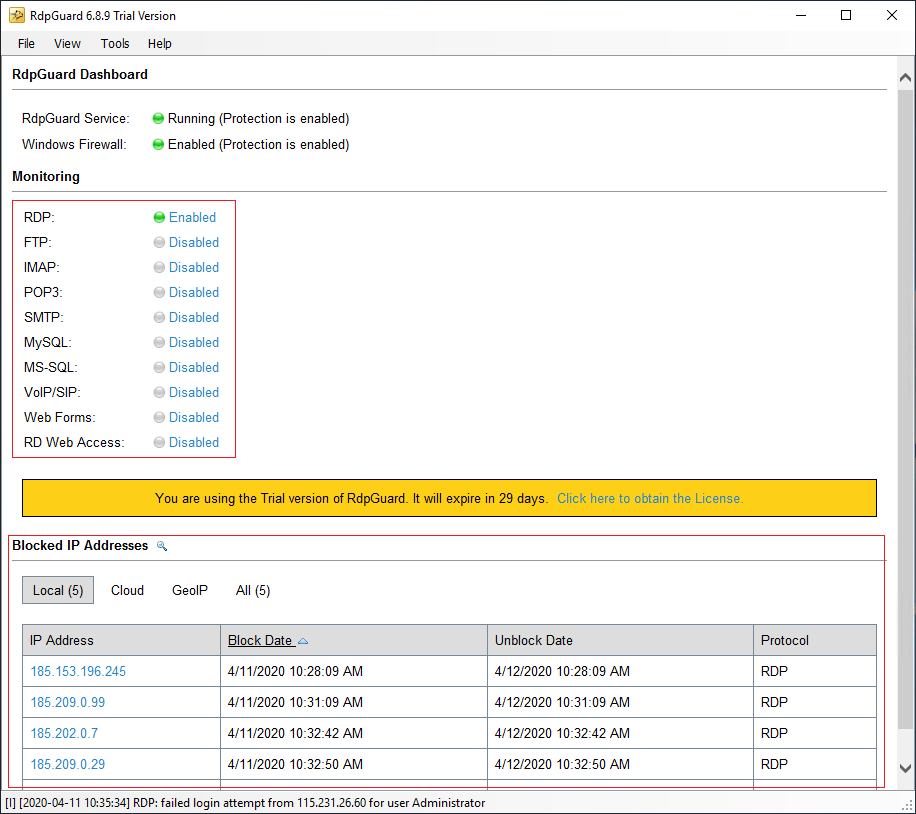
And if you wish to activate the protection for another service, you can easily choose “Disable” behind any service to enable it. For example, now we will activate protection for FTP service.
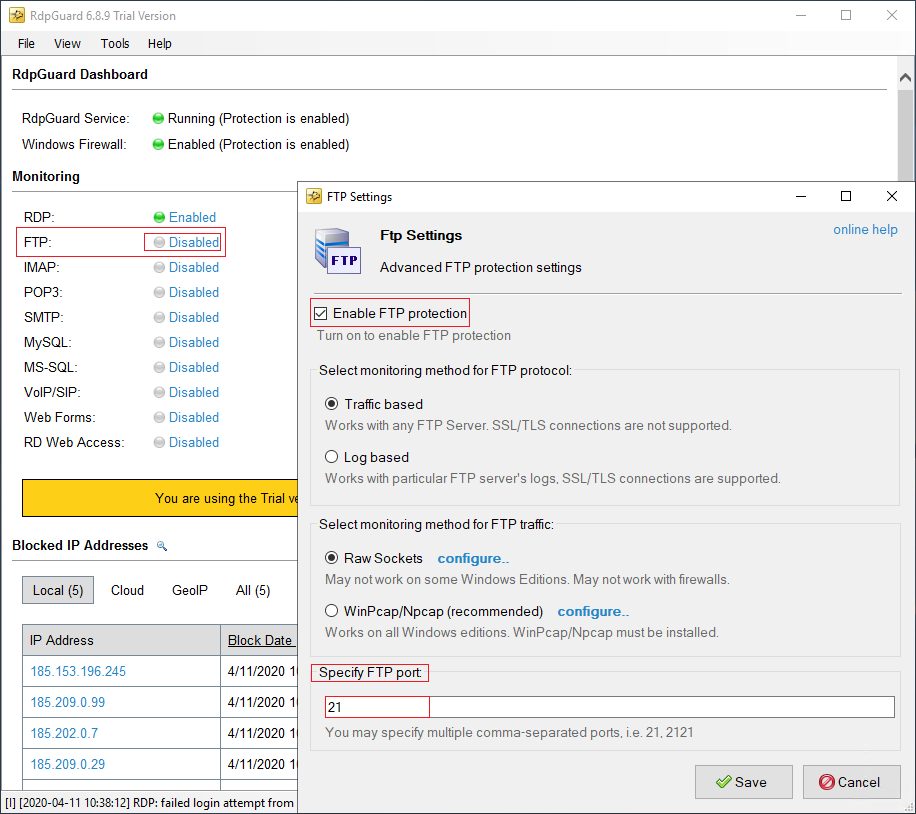 You can check “Enable FTP Protection” and configure the mentioned setting to activate the protection on the new page. You can activate protection for other services as well as this one.
You can check “Enable FTP Protection” and configure the mentioned setting to activate the protection on the new page. You can activate protection for other services as well as this one.
Conclusion
After you buy RDP, it can be hacked easily if you don’t be careful about some cases, and one of these cases was brute-force attacks that we talked about how to stop it.
To detect and prevent DDoS attacks on different systems, you can also check the below link:
Detect And Prevent DDoS Attacks
How do you think about preventing brute force attacks on RDP?
Please share your ideas with us in the comments section.
It's going to be end of mine day, but before end I am reading this enormous piece of writing to increase my experience.