What is TLS Understanding Secure Internet Connections
TLS (Transport Layer Security) is a security protocol that encrypts data sent over the internet. It protects information between web servers and clients. TLS helps prevent unauthorized access during online communication.
TLS, by using various cryptographic techniques, has an important role in establishing a secure connection between clients and servers such as web browsers and web servers, servers and web applications; it is also widely used in other online services such as VPN, email, messaging, and voice over IP (VoIP) to achieve security.
🤖 AI Overview:
What is TLS? TLS stands for Transport Layer Security and is a protocol that protects data by encrypting it when information is sent over the internet. Its main purpose is to keep communications secure and private between computers and servers. TLS is widely used for web browsing, email, and other online services to prevent unauthorized access.
Checklist:
- Identify TLS as a security protocol that encrypts data for secure online communications.
- Confirm TLS protects privacy, ensures data integrity, and authenticates server identities.
- Check for a padlock in your web browser address bar to know TLS is active.
- Use TLS for web browsing, email, file transfers, VPNs, and secure messaging.
- Update to the latest TLS version, such as TLS 1.2 or TLS 1.3, for improved security.
- Install a TLS certificate on your website to safeguard sensitive user data.
- Replace outdated SSL protocols with TLS for stronger site protection.
- Regularly review your TLS setup to prevent vulnerabilities and maintain trust.
What does TLS do?
TLS provides privacy and integrity of sensitive data transmitted between two communicating applications and protects data from eavesdropping, tampering, and other security threats through its three main components:
Encryption:
TLS makes data unreadable to anyone by encrypting all data exchanged over the network. This safeguards sensitive information like passwords and credit card numbers from third-party monitoring.
Authentication:
TLS verifies the identity of websites and applications that exchange information with you to prevent you from interacting with fake or malicious sites.
Data integrity:
TLS ensures that attackers have not altered or tampered with data during transmission.
How does TLS work?
TLS works by establishing a secure connection between a client and a server through TLS handshake protocol and TLS record protocol, which use symmetric and asymmetric cryptography methods.
TLS to secure communications through encryption and identity authentication relies on the handshake protocol, which generates public and private keys using asymmetric encryption.
Asymmetric encryption in TLS works so that both public and private keys are needed to decrypt encrypted data.
How is a TLS handshake executed?
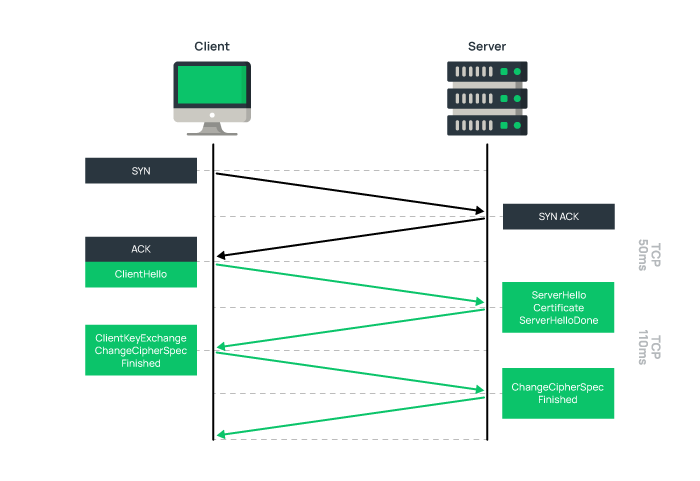
The TLS security process through TLS handshake is as follows:
1. TLS handshake starts with the server and client agreeing on the encryption method and credentials exchange. For this purpose, the initial message “Client Hello” is sent from the client to the server, including the TLS version and the encryption algorithms supported by the client.
2. To establish a connection, the server usually proves its identity with a trusted TLS certificate and sends the TLS certificate along with the public key to the client with a “server Hello” message for the authentication process.
3. After verifying the server’s TLS certificate, the client generates a pre-master key from the server’s public key, which is decrypted by the server’s private key.
4. When both the server and the client device have a symmetric (master) key for encryption and decryption, the handshake process ends.
5. Also, to verify the integrity of the data, authenticated and encrypted data is signed with a Message Authentication Code (MAC). Therefore, the client confirms the data integrity upon receiving the MAC message.
What is TLS used for?
- Secure web browsing (HTTPS)
- Email Encryption
- Secure File Transfer via FTPS (FTP over TLS) or SFTP (SSH File Transfer Protocol)
- VPN for establishing secure connections between a client and a VPN server
- Secure APIs and Web Services
- Instant messaging and video conferencing
- Instant messaging and video conferencing
What is a TLS certificate?
TLS certificate, also known as SSL certificate, is digital document that is issued by a certificate authority to business or person and verifies authenticity of a website or server.
TLS certificate is needed for secure communication over the internet and contains important information such as website’s domain name and public key for encryption and validating the server’s identity.
The padlock icon next to the website address bar in the browser ensures you connect to the secure and correct site.
What is the difference between TLS and SSL?
TLS is the upgraded version of SSL and was developed from SSL (Secure Socket Layers), which is designed for securing web sessions.
SSL is the predecessor model of TLS and older technology, which had some security flaws.
TLS was developed to fix SSL security vulnerabilities by supporting improved encryption and authentication mechanisms.
So TLS as successor to SSL, provides stronger security and improved performance compared to SSL and is also compatible with modern applications and services.
Is TLS more secure than SSL?
Yes, since TLS is newer and, by fixing vulnerabilities found in older SSL versions, became a successor to SSL, TLS is more secure than SSL.
TLS supports more advanced encryption algorithms and more efficient authenticates than SSL.
Also, all SSL versions are deprecated and are not supported by most browsers.
What is the difference between TLS and HTTPS?
TLS is a security network protocol that establishes encrypted communication with an authenticated peer over the Internet. HTTPS is a special implementation of TLS within web communication, which nowadays HTTPS all websites and some web services benefit from.
HTTPS uses TLS on top of HTTP; unlike TLS, which is used for various communications, HTTPS is a secure web browsing method.
Why is the TLS protocol important for Web apps and businesses?
- TLS End-to-end encryption protects your sensitive data and web applications from data breaches, eavesdropping, tampering, and other attacks.
- Through authentication support, TLS provides privacy and data integrity, which prevents man-in-the-middle attacks and ensures that unchanged data is transmitted.
- TLS helps Improve SEO due to the importance of Website security in Google ranking. So, TLS brings a competitive edge to a business site’s ranking on search engines.
- TLS protocol creates a secure web browsing experience for users and will attract customers’ trust to your business site. So customers can trust your business site for data exchange, like making online purchases or creating a new account.
- Through its powerful alert system, TLS alerts users immediately of any problems and errors.
- TLS-protected HTTPS has become a standard method for securing websites and web services.
Is TLS secure?
TLS is one of the most secure protocols to establish secure communication globally across the Internet. However, keeping TLS updated and properly configuring is good practice to ensure security.
Like other technologies, TLS does not guarantee 100% security. For this reason, you should use more advanced security layers, such as VPNs, to enhance security.
Configuring your own VPN on VPS and using the TLS protocol in the VPN for a secure and encrypted connection is good practice; Our VPS servers meet your needs.
Where can TLS be implemented?
TLS operates (can be implemented) at the OSI model’s transport layer and on top of TCP to apply encryption on application layer protocols such as HTTP, FTP, SMTP, and IMAP.
For VPN and SIP-based applications, TLS can operate on UDP, DCCP, and SCTP.
How does TLS secure communication?
TLS employs various security mechanisms, including mechanisms for cryptographic (symmetric encryption, asymmetric encryption, and hash functions), authentication, key exchange, encryption, and integrity checking to provide secure communication.
What is the most recent version of TLS?
TLS 1.3 is the most recent version of TLS, published in 2018.
TLS was published in RFC 2246 in 1999 and has evolved over time, with several versions to improve its performance and security vulnerabilities released.
TLS 1.2 and TLS 1.3 are the most common and latest versions of TLS, which are vital for any organization to benefit from the latest security enhancements.
What is the impact of TLS on web app performance?
TLS imposes slight latency and performance overhead due to TLS’s complex encryption and decryption processes. So, you may experience a decrease in web application loading time and server and client memory.
However, Modern TLS versions have minimized this impact on web application performance. Moreover, you can use technologies like TLS False Start and TLS Session Resumption to speed up TLS connection.
What is DTLS?
DTLS (datagram transport layer security), like TLS, is a security protocol for communication that is designed to guarantee security for datagram-based applications over unreliable networks.
DTLS works with the UDP (User Data Protocol) to provide security guarantees in communications.
DTLS is commonly used in real-time communication applications like online gaming, VoIP (internet telephony), IoT devices, video conferencing, and VPNs.
Is TLS outdated?
In 2021, internet standards and regulatory bodies deprecated TLS 1.0 and 1.1.
However, TLS 1.2 and TLS 1.3 are allowed to be used, and businesses can benefit from these versions of TLS.
What are the TLS risks?
Using outdated versions, weak ciphers, and improper setup of TLS can make data vulnerable to attackers and leave loopholes for potential attacks such as man-in-the-middle (MITM) or downgrade.
Although TLS is high-tech in security terms, you can mitigate these risks with updates and strong encryption configuration.
Do I need to use TLS?
TLS is essential to secure and encrypt your data, especially when transmitting important information.
TLS/SSL certificate is highly recommended for business websites to protect their and customer sensitive data like personal information, financial details, or login credentials from eavesdropping, tampering, and other malicious activities.
Important points about TLS
- Based on certificate-based encryption
- Commonly used for handling HTTPS
- Various encrypted protocols are also based on TLS (e.g. SIPS or H.323 TLS for encrypted IP telephony, LDAPS for databases, DTLS for webRTC etc.)
- Attackers cannot access the encrypted data stream.
FAQ
How does TLS work to protect my data?
TLS works by encrypting the data exchanged between your device and a website. This means that information is converted into a secure code, making it accessible only to the intended recipient and protecting it from unauthorized parties.
What is the difference between TLS and SSL?
TLS is an upgraded and more secure version of the earlier Secure Sockets Layer or SSL protocol. While people often use the terms interchangeably, TLS provides stronger security features and is the standard used today.
How can I tell if a website is using TLS?
You can identify if a website uses TLS by looking for a padlock icon in the address bar of your web browser and a URL that begins with “https”. This indicates that your connection is encrypted and protected with TLS.
What are the main benefits of using TLS for websites and users?
The main benefits of TLS include data encryption, secure authentication of websites, and protection from cyber threats such as eavesdropping, data tampering, and unauthorized access. This builds trust between users and online services.
Do all websites use TLS and should I avoid those that do not?
Not all websites use TLS, but it is highly recommended for all sites, especially those handling personal or financial information. Visiting websites that do not support TLS can put your data at risk, so it is best to avoid them whenever possible.
Is it possible for TLS to be compromised and how can I stay protected?
While TLS is highly secure, vulnerabilities can arise if it is not properly implemented or updated. Using the latest versions of browsers and avoiding outdated protocols are effective ways for users to stay protected.
Does using TLS affect website speed or performance?
TLS may add a small amount of processing time due to encryption, but for most modern websites, the effect on speed is minimal. The security benefits significantly outweigh any slight delay.
How often is TLS updated and who is responsible for maintaining it?
TLS protocols are regularly updated to address new security risks and enhance performance. Website owners, hosting providers, and administrators are responsible for ensuring that their servers support the latest TLS versions.
Can TLS protect me from all types of online threats?
TLS provides robust protection for data during transmission but it does not guard against all online threats such as malware or phishing scams. It is important to use additional security practices like strong passwords and updated antivirus software alongside TLS.
Conclusion
TLS is like a high-tech lock for your online activities; it encrypts your data and keeps them secret.
TLS is essential for every business on the internet to protect business and customer-sensitive data from prying eyes and other attacks.
TLS ensures you connect to real websites and allows you to browse online confidently.