How to Add a Domain Controller in Windows Servers
Domain Controller in Windows manages network security by authenticating users within an Active Directory domain. It centralizes user management, ensuring secure access and seamless network communication.
🤖AI Overview:
A Domain Controller in Windows securely manages user authentication and resource access within an Active Directory domain. Adding domain controllers in Windows Server versions 2016, 2019, and 2022 enhances network reliability, fault tolerance, and load balancing by providing redundancy and continuous service access.
Prerequisites to Add a Secondary Domain Controller
Before you begin adding your secondary domain controller to your existing Active Directory environment, it’s critical to prepare the server to avoid potential configuration errors and ensure a smooth deployment.
- Server Name: Assign a unique and meaningful computer name to the server. Avoid changing the name after promoting it to a domain controller, as it may cause domain-wide issues.
- Static IP Address: Configure a static IP for the server and ensure that the DNS settings point to an existing domain controller or DNS server. Without this, the server cannot communicate properly within the domain.
- Accurate Time Settings: Check that the time and time zone are correct. Inconsistent time settings can lead to Kerberos authentication errors and disrupt domain operations.
- Host Active Directory or Windows Server: Consider opting for a Windows VPS to gain dedicated resources, enhanced performance, and a scalable solution tailored to your needs.
- Ensure you have the PowerShell command line tool ready and administrative privileges to run scripts.
Set Up Additional Domain Controller in Windows Server 2016,2019, 2022
Adding a secondary domain controller (DC) to your Windows Server environment is a crucial step to enhance redundancy, boost security, and ensure the seamless operation of your Active Directory infrastructure.
Whether you are using Windows Server 2016, 2019, or 2022, this guide will walk you through the process with clear explanations and best practices.
Step 1: Install Active Directory Domain Services Role
Follow the below path to install AD DS Role:
- Open Server Manager and click on Add roles and features.
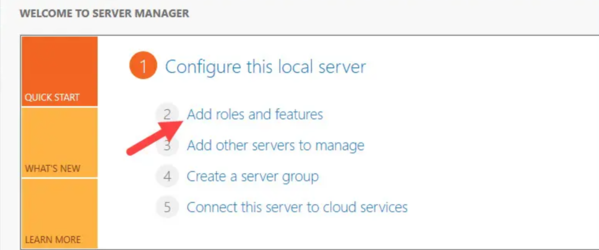
- On the “Before you begin” page, click Next.
- Choose Role-based or feature-based installation and click Next.
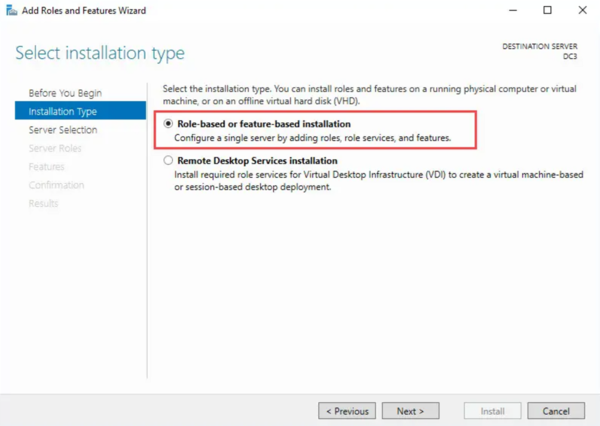
- Choose your server from the list and proceed by clicking Next.
- Select Active Directory Domain Services (AD DS) and confirm by clicking Add Features when prompted.
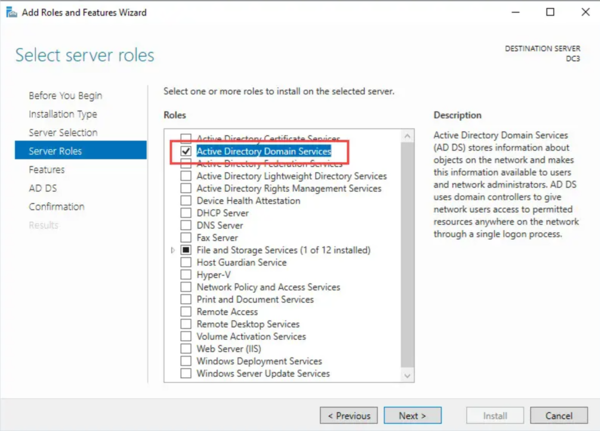
- On the Features page, click Next as no additional features are required.
- The AD DS page provides an overview of the role. Click Next to continue.
- Click Install on the confirmation page.
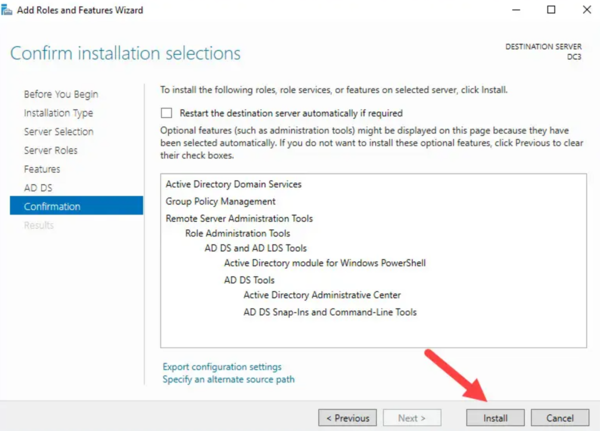
- After installation, a message will indicate that additional configuration is required.
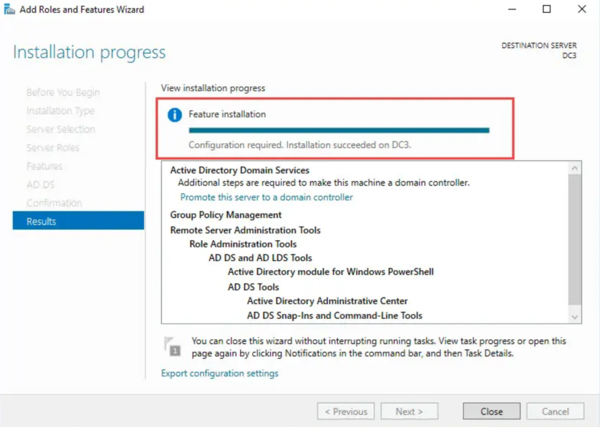
Step 2: Promote the Server to a Domain Controller
Follow the below actions to pass this step:
- Click the yellow warning flag in Server Manager and select Promote this server to a domain controller.
Note: For more information on this process, check out our guide on setup Active Directory Domain Services in Windows server.
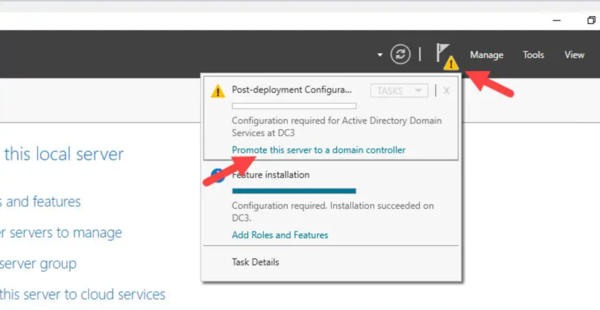
- Choose Add a domain controller to an existing domain. Enter the domain name and provide credentials with sufficient privileges to modify the domain. Click Next.
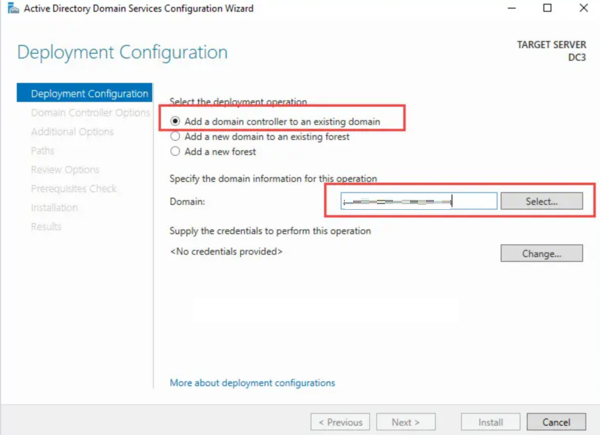
- To set Domain Controller Options, Ensure DNS Server and Global Catalog (GC) are selected.
- Use the default site name unless a specific site configuration exists.
- Set a strong Directory Services Restore Mode (DSRM) password. This is essential for troubleshooting or recovering the AD database.
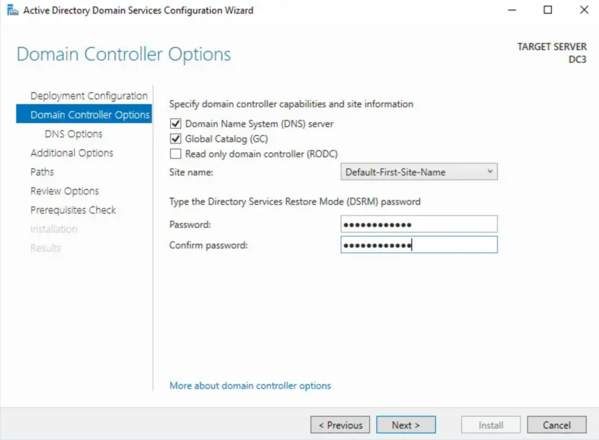
- If you see a warning about DNS delegation, it can be safely ignored unless your setup requires external DNS delegation.
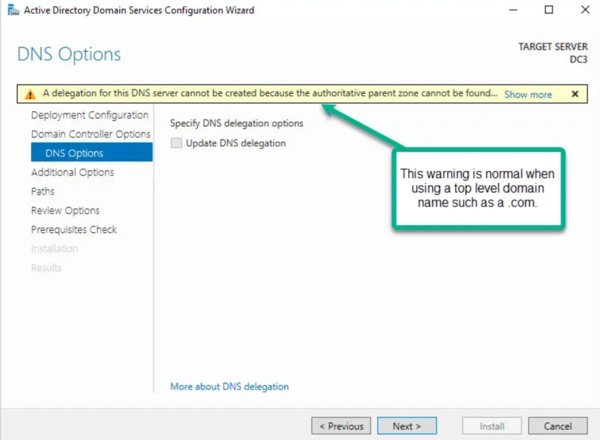
- Choose a replication source. If your environment has multiple domain controllers in the same site, select Replicate from any domain controller.
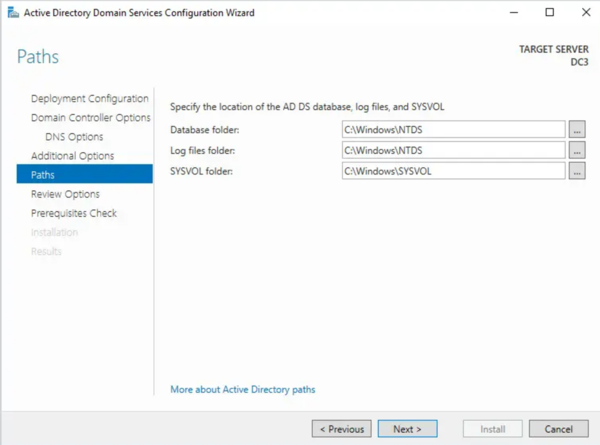
- Leave the database, log files, and SYSVOL paths at their default locations unless you have specific requirements.
- On the review page, confirm the settings. Address any warnings on the Prerequisites Check page (e.g., cryptographic algorithm compatibility). If all checks pass, click Install.
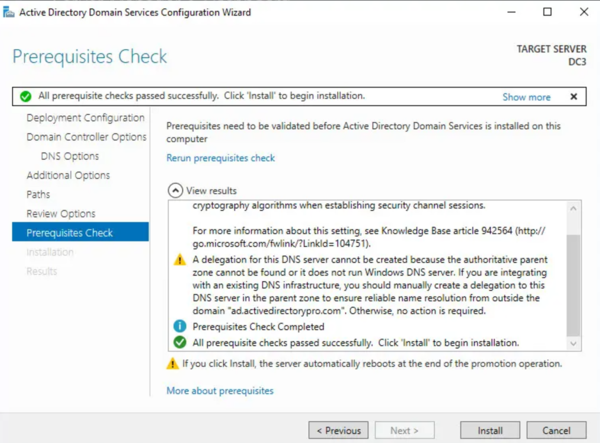
The server will automatically reboot once the installation is complete.
Step 3: Verify the Secondary Domain Controller
After the setup, it’s crucial to verify that the new domain controller has been successfully added and is functioning as expected:
- To check Active Directory Replication, open a command prompt and run
repadmin /replsummaryto confirm that replication between domain controllers is error-free. - To inspect Active Directory Health, use
dcdiag /vto perform a detailed health check of the domain controller. Review the output to ensure all services are operational. - Finally, open Active Directory Users and Computers (ADUC) and confirm that users and computer objects have been replicated to the new domain controller to verify in ADUC.
Step 4: Configure DNS Servers
Proper DNS configuration is critical for seamless domain functionality:
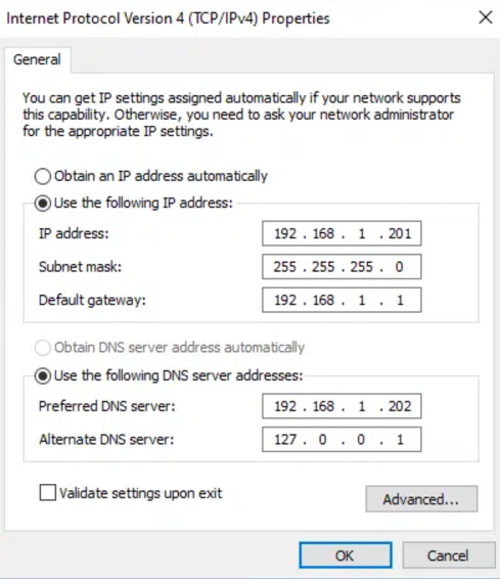
- On each domain controller, set the Preferred DNS Server to point to the other domain controller.
For example, DC1’s preferred DNS server should point to DC2’s IP address.
- Set the Alternate DNS Server to point to its IP address or the loopback address (
127.0.0.1).
*********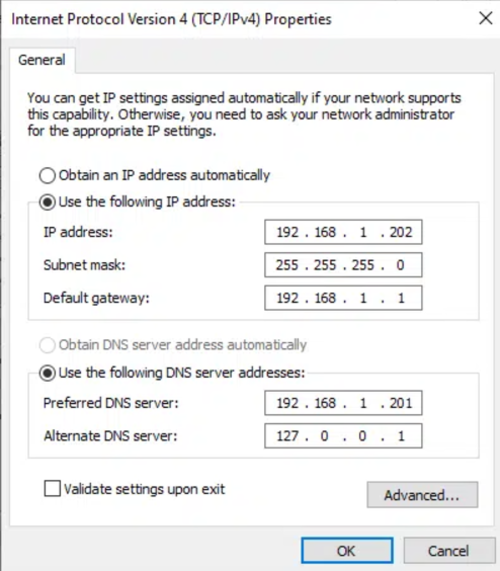
This ensures redundancy and prevents potential disruptions in name resolution across the domain.
Adding a secondary domain controller helps balance the load, enhances fault tolerance, and ensures that if your primary DC goes down, your network continues to run smoothly.
Quick Guide to Install AD DS Using Windows PowerShell
Using Windows PowerShell to install Active Directory Domain Services (AD DS) is an efficient and script-driven approach, particularly beneficial for administrators who prefer automation or remote server management.
Below are the step-by-step instructions, each succinctly explained, along with the appropriate commands.
Step 1: Configure Basic Server Settings
Before diving into the installation, ensure your server’s computer name, static IP address, and time zone are properly configured.
This aligns with best practices for domain setup, avoiding future connectivity issues.
Rename-Computer -NewName "DC2" -RestartStep 2: Install the Active Directory Domain Services Role
Use the Install-WindowsFeature cmdlet to install the AD DS role along with management tools.
This is equivalent to adding the role via Server Manager:
Install-WindowsFeature AD-Domain-Services -IncludeManagementToolsStep 3: Verify Role Installation
After installation, confirm the AD DS role is properly installed by checking the installed Windows features:
Get-WindowsFeature | Where-Object { $_.Installed -eq $true }Step 4: Promote Server to a Domain Controller
Promote the server by creating a new forest, adding it to an existing domain, or making it an additional domain controller.
Use the Install-ADDSDomainController cmdlet for this purpose:
Install-ADDSDomainController -DomainName "yourdomain.com" -Credential (Get-Credential) -InstallDns -SafeModeAdministratorPassword (ConvertTo-SecureString "YourPassword123" -AsPlainText -Force)This command integrates the new server into the domain, sets up DNS, and secures the restore mode password.
Step 5: Configure DNS Servers
Ensure that DNS settings on both domain controllers are appropriately configured for redundancy:
- Preferred DNS: Points to the other domain controller.
- Alternate DNS: Points to the local IP address or
127.0.0.1.
Set-DnsClientServerAddress -InterfaceAlias "Ethernet" -ServerAddresses ("192.168.1.2","127.0.0.1")Step 6: Validate AD DS Installation
Run diagnostic tests to ensure the AD DS and replication configurations are successful:
- Replication Summary:
repadmin /replsummary- Health Check:
dcdiag /vWhy Use PowerShell for AD DS Installation?
PowerShell offers automation, speed, and consistency, especially when managing multiple servers or configuring a large network.
Moreover, its scriptable nature minimizes manual errors, providing a streamlined alternative to Server Manager.
Why add a Secondary Domain Controller in Windows?
A secondary domain controller isn’t just a backup; it’s a lifeline for your Active Directory.
Sharing the load of authentication requests and directory lookups improves performance while ensuring that operations continue even if the primary domain controller experiences issues.
Organizations aiming for network reliability, failover support, and increased security should prioritize adding a secondary DC to their infrastructure.
How to solve “The specified domain either does not exist or could not be contacted” Error?
This error often indicates a DNS issue or connectivity problem with the existing domain controller. To troubleshoot it:
- Verify that the server has network access to the current DC and that DNS settings are properly configured.
- Ensure that the domain name is correctly typed and that the DNS server is pointing to a functioning domain controller.
- Check that the Netlogon service is running on all involved domain controllers.
How to Troubleshoot AD DS installation fails due to missing prerequisites?
Sometimes, when installing AD DS, you may see errors regarding missing prerequisites such as incorrect functional levels.
To resolve this, ensure that your domain’s functional level supports the version you are upgrading to (e.g., Windows Server 2008 R2 or higher for Windows Server 2016/2019).
You may need to run the adprep /forestprep and adprep /domainprep commands on the existing domain controller before you proceed.
How to verify if a domain controller was added successfully?
Use PowerShell or Active Directory Users and Computers (ADUC) to confirm the new domain controller is listed and functional.
Running the Get-ADDomainController command will show all DCs in the domain.
Additionally, ensure that Replication is working by using the repadmin /showrepl command.
How to troubleshoot if the new domain controller is not replicating?
Verify that the DNS settings are correct, and ensure the SYSVOL and NETLOGON shares are properly shared.
Also, check for network issues or firewall restrictions. You can force replication with the repadmin /syncall command or troubleshoot using Event Viewer for more detailed error messages.
Conclusion
Deploying and managing a domain controller in Windows is a strategic investment for business owners aiming to safeguard their IT infrastructure. By centralizing authentication, enhancing security, and providing redundancy through additional controllers, organizations achieve a resilient Active Directory environment.
Whether you prefer the graphical interface of Server Manager or the automation strengths of PowerShell, following established best practices ensures an efficient and secure setup. Proper configuration, verification, and ongoing maintenance empower your business with uninterrupted network services, improved security, and scalability for future growth. Incorporating a secondary domain controller is not just a technical task but a critical step toward sustainable IT management and operational excellence in Windows Server domains.
FAQ
2. How does adding a secondary Domain Controller benefit my business network?
It provides redundancy, load balancing, and fault tolerance, improving network reliability and continuous resource access.
3. What are the steps to install a Domain Controller using Server Manager?
Install the Active Directory Domain Services role, promote the server to Domain Controller, and configure DNS and replication settings.
4. Can I install a Domain Controller using PowerShell, and what are the advantages?
Yes, PowerShell automates installation and promotion, offering speed, consistency, and reduced manual errors for multiple servers.
5. What prerequisites are needed before adding a secondary Domain Controller?
Ensure a unique server name, static IP, correct DNS settings, synchronized time, and administrative privileges.
6. How do I verify a Domain Controller was successfully added?
Use repadmin and dcdiag to check replication and health, and confirm in Active Directory Users and Computers.
7. Why is correct DNS configuration critical for a Domain Controller?
DNS is essential for domain operations; misconfiguration can cause communication failures and authentication issues.
8. What common errors can occur during Domain Controller installation, and how are they resolved?
Issues include DNS misconfiguration, network problems, and missing prerequisites; resolving involves verifying settings and running domain prep commands.
9. How do Domain Controllers differ across Windows Server versions 2016, 2019, and 2022?
Later versions include enhanced security, improved replication, and updated management tools.
10. What role does a Domain Controller play in securing IT infrastructure?
It enforces authentication policies, manages access rights, and centralizes security management to protect business data.