10 Differences Between Hardware And Software Firewall
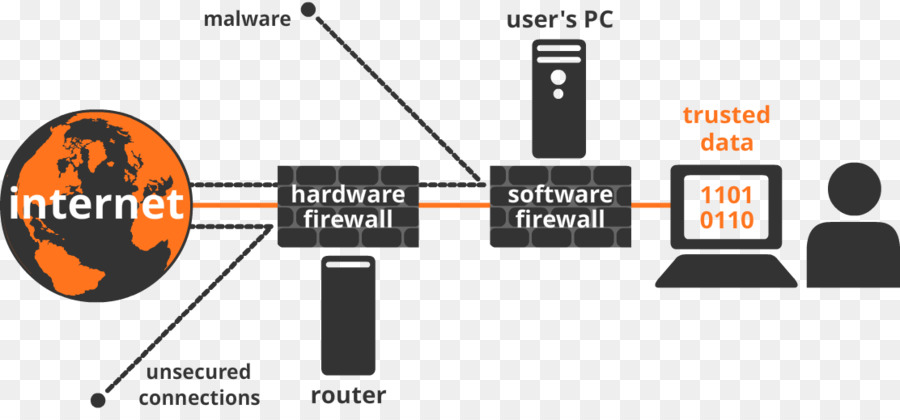
Firewall models can be divided into two groups: a software firewall and a hardware firewall. Firewall software is a security software that is installed on a computer or server. A hardware firewall is a standalone device with a dedicated CPU, memory, operating system, and software. Some hardware firewalls are also part of the router and are integrated into it.
The difference between software firewalls and hardware firewalls is rooted in their capabilities. Due to the differences between the hardware firewall and the software firewall and the advantages and disadvantages of each, both firewalls can be used in networks to compensate for the other disadvantages.
What Is A Firewall Exactly?
A firewall is a software or hardware that, like a security fence, surrounds a network or computer system and protects them from certain cyber threats. A software or hardware firewall can be considered the first security barrier to network input. Therefore, any data must first pass through the firewall before it can reach your network from the Internet or other networks. But how does a firewall detect what should and should not cross the network boundary?
For this purpose, the firewall checks the data packets, including the source and destination addresses of the packets, complies with the set of rules defined for the network, and then determines whether the packet is allowed to pass. By setting up a firewall, malicious sites can be blocked to prevent unauthorized access or the entry of viruses and other malware into the network. Firewalls are either software or hardware.

What Is A Software Firewall?
A firewall is a software that is installed on a computer or server. One of the most popular software firewalls is the proprietary firewall for the Windows VPS operating system, which is accessible from the Windows Security Settings screen or Pfsense for Linux VPS. In addition, security software companies (Kaspersky, Panda, etc.) also produce their own firewalls, which usually come in different versions. Some of them are designed for personal computers and others are designed for installation on network servers and enterprise environments.
So that with just one installation on the server, other network computers will be under its security umbrella because otherwise, it should be worth every computer connected to the network. , Buy and install a separate firewall, which obviously costs a lot and will take a lot of time to install and run on tens or hundreds of computers. In addition to monitoring incoming network traffic, some software firewalls can also monitor outgoing network traffic. In addition, software firewalls usually have more security options and settings and are more flexible.
Advantages Of A Software Firewall
- Home software firewalls are usually cheap and some are even free. Their professional and corporate versions also have multi-user licenses and can, therefore, cover all systems on a network.
- Installing and configuring regular versions of software firewalls is simple, and the required level of security can be determined with just a few clicks. But organizational versions require more knowledge and expertise.
- Some software firewalls can monitor and refine network outbound traffic in addition to incoming traffic, and in this respect are superior to hardware firewalls.
- Software firewalls are more flexible. For example, using them can limit the access of some programs to the network and thus reduce the possibility of some malware infiltration.
- Software firewalls, especially single-user versions, are more removable because they are installed on a computer, meaning that the computer comes with a firewall wherever it goes. This feature is important for those who often travel with a laptop.
Disadvantages Of Software Firewall
- The software firewall uses the resources (CPU, memory, etc.) of the host system and as a result, may reduce its speed or performance.
- The more computers and systems available on the network, the higher the cost of purchasing software firewalls is. As the use of single-use software firewalls on such networks is not cost-effective or time-consuming, you must purchase a copy that supports all systems. In addition, cheap or free firewalls are usually not very effective in sensitive and corporate environments.
What Is Hardware Firewall?
A firewall is a stand-alone hardware device that has a dedicated processor, memory, and operating system. Due to the fact that in many medium and large networks, servers and other network equipment are installed inside the rack, some stand-alone hardware firewalls are designed to be installed in server racks and therefore have a standard size. Some hardware firewalls are also part of a network router instead of a standalone device. In other words, some network routers also have an internal hardware firewall.
The hardware firewall is located at the network boundary, ie between the router and the outside world (Internet or other networks). Therefore, it is the first line of defense at the entrance to the network. Any data must go through the hardware firewall before it reaches the router and then the computers on the network.
Another advantage of a hardware firewall rather than a software firewall is that it hides the computer or local area network from the outside world. So the external monitor sees only a hardware device instead of the network that has an unfamiliar operating system (because it was said that the operating system of the hardware firewalls is proprietary). This method of secrecy is called network address translation (NAT). Of course, this measure does not work against the entry of e-mail viruses.
Advantages Of Hardware Firewall
- The hardware firewall defends the network one step ahead of the software firewall because the software firewall is installed on a computer or network server, but the hardware firewall is located even before the router and right on the network border.
- A hardware firewall can cover an entire network. This feature is very valuable and financially cost-effective in centers that have many computers.
- Independent hardware firewalls such as CPUs, memory, and proprietary operating systems that do not install on another computer are more efficient and faster than software firewalls.
- Hardware firewalls are more resistant to malware because their operating system is different from common operating systems such as Windows, which is more popular with hackers.
Disadvantages Of Hardware Firewall
- Configuring enterprise hardware firewalls is difficult for beginners.
- Hardware firewalls are not suitable for monitoring outbound traffic.

What Is The Difference Between Software Firewall And Hardware Firewall?
The hardware firewall is the first line of defense against network inputs and is superior to the software firewall in that it monitors incoming traffic before it even reaches the network router. But the software firewall is installed on the computer or network server, and as a result, incoming traffic is forwarded to the computer or network server before it is monitored. In contrast, hardware firewalls are not suitable for monitoring network outbound traffic, while some software firewalls also monitor outbound traffic.
Of course, monitoring outbound traffic is not uncommon because it can sometimes be challenging. For example, monitoring outbound traffic may interrupt the application software used in the network and disrupt the organization’s workflow. So the firewall configuration should be such that the work of the collection is not disrupted.
Inbound Firewall And Outbound Firewall
A firewall set up to monitor incoming traffic is called an inbound firewall, and a firewall set up to monitor outbound traffic is called an outbound firewall. Some firewalls are capable of monitoring both types of traffic. By default, firewalls only monitor and filter only incoming network traffic, as it is often assumed that the network is being threatened from the outside and is facing cyber threats from the outside in.
If so, monitoring incoming traffic is sufficient to secure the network. But sometimes in some networks (such as important organizational networks), it is necessary to monitor and refine the network output traffic. Imagine a user unknowingly requesting something from outside the network (outbound traffic) in response to which malware is sent to the network (inbound traffic). Or imagine malware that has already penetrated the network (inbound traffic) and now wants to send out organization data while connected to the Internet (outbound traffic). So sometimes monitoring and refining outbound traffic is just as necessary as monitoring inbound traffic.
As mentioned, a software firewall is commonly used to monitor network outbound traffic. A software firewall usually has a ready-made list of secure applications. If an application that is not listed in the firewall is authorized, the firewall will ask you if you want to allow that application to connect to the Internet. As explained, it is sometimes recommended to use both a software firewall and a hardware firewall to cover each of the other shortcomings.

Various Firewall Configurations
After installing the firewall, different configurations can usually be done. The firewall can be configured to monitor and refine network traffic according to various criteria, including:
- IP-based monitoring: IP addresses are 32-bit numbers assigned to each web address.
- Content-Based Monitoring: A firewall can be configured to open only certain websites on the network or to block certain websites (such as social networks).
- Domain Name Monitoring: A firewall can be configured to allow websites based on their domain name or not.
- Protocol-based monitoring: A firewall can determine how a user accesses an online service.
- Port-based monitoring: Network servers make their services available to users through ports that each have a specific number. For example, a web server may be configured on port 80.
- Keyword or phrase monitoring: You can make the firewall sensitive to certain words or phrases to block websites that contain those words and phrases.
- Behavior-based monitoring and changes: The firewall can detect and prevent suspicious behavior. Sudden deletion of data or hacking attacks is among the suspicious behaviors.
The firewall is configured in different ways. It is possible to decide which method is more effective by consulting an IT expert. For example, one way is to temporarily block access to everything and then set the permissions one by one.
The Firewall Is Not Enough
Firewalls, despite their capabilities, are not always effective against any threat. Sometimes some security software and human considerations are needed to further improve the security of the collection. Firewalls do not always protect the user from social engineering attacks or spoofing attacks. For example, a hacker may impersonate a customer and gain company information by deceiving users. In such cases, firewalls usually do not work, and email monitoring software is more efficient.
Also, firewalls do not always prevent malware, viruses, and worms from entering. For this purpose, anti-virus programs should also be used so that if the malware can pass through the firewall, the anti-virus software can deal with it. But even with these measures, network security cannot be fully guaranteed. So network users should increase their knowledge in the field of cybersecurity as much as possible because sometimes trained people are the best security barrier and people with little information are the biggest threat to their network.
I hope you’ve enjoyed this post.
Please do not hesitate to share your opinions with us.