How to Secure Nginx on Debian 10/11
An easy way to secure nginx on Debian 10/11 is using a Certificate Authority called Let’s Encrypt. CA provides a method to obtain and install free TLS/SSL certificates. It also enables encrypted HTTP on web servers. The process of installing and obtaining certificates is fully automated on Nginx. Developed by ISRG, Let’s Encrypt is a free and open certificate authority that provides free SSL certificates. All major browsers trust the certificates of Let’s Encrypt which are valid for three months from the issue date.
This article will use the easy-to-use tool of Cerbot to obtain a free SSL certificate to secure Nginx on Debian 10/11. Also, a separate Nginx server block file will be used instead of the default one. To maintain the default files as a fallback configuration, you can create new Nginx server block files for each domain.
Prerequisites to Secure Nginx on Debian
To let this tutorial work correctly, consider the below options and move on to secure Nginx on Debian 10/11.
- A Linux VPS hosting running Debian.
- A non-root user with
sudoprivileges. - A domain that points to your public server IP that obtains the SSL certificate.
Tip: In this guide, your_domain points to your public IP address of the server, and www.your_domain points to your server’s public IP address.
Tutorial Secure Nginx on Debian 10/11
To secure Nginx on Debian 10/11, you need to install a free Let’s Encrypt SSL certificate. As we mentioned, we use Cerbot to obtain and renew the certificates. Certbot is a fully-featured utility that automates the tasks of obtaining and renewing Let’s Encrypt SSL certificates and configuring web servers to use the certificates.
Join us to go through the steps of this guide and secure Nginx on Debian 10/11.
Step 1. Install Cerbot
The first step to secure Nginx on Debian is to install Cerbot. While Cerbot is included in the default Debian repositories, run the following commands to install it.
sudo apt updatesudo apt install python3-certbot-nginxRunning the above commands makes Cerbot ready to use on your Debian server. Just confirm some of Nginx’s configuration to help it configure SSL for Nginx.
Step 2. Verify Nginx’s Configuration
As you know, Cerbot needs to find the proper server block in your Nginx configuration to be able to configure SSL automatically. So, use your favorite editor to open the server block file for your domain to confirm it. Here, we use nano.
sudo nano /etc/nginx/sites-available/your_domainTo find the correct server block, search for server-name line which matches your requested domain that is something like the below:
/etc/nginx/sites-available/your_domain
...
server_name your_domain www.your_domain;
...If you received the above result, you’re all set. But if not, you need to update it. The block file must be reopened to be checked if you get an error to correct any typos or missing characters.
However, to move on to the next step, save the file and quit your editor, and to verify the syntax of your configuration edits run:
sudo nginx -tWhen you have a correct configuration file, use the command below to reload Nginx and load the new configuration:
sudo systemctl reload nginxIn this way, the correct server block can be found and updated by Cerbot. There are three steps remaining to secure Nginx on Debian. Stay with us.
Step 3. Change the Firewall settings for allowing HTTPS traffic
In this part, you must allow HTTPS traffic and update the firewall. If you have the ufw firewall enabled, adjust the settings to allow for HTTPS traffic. So, firstly, use the following command to view the current setting.
sudo ufw statusWhen you see the status is active in your output, you can make sure that only HTTP traffic is allowed to the web server.
Then, allow the Nginx Full profile and delete the redundant Nginx HTTP profile allowance.
sudo ufw allow 'Nginx Full'
sudo ufw delete allow 'Nginx HTTP'You must have a status like this:
sudo ufw status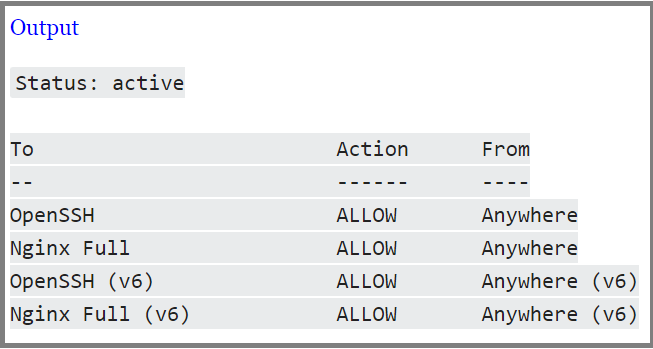
Step 4. Obtain an SSL certificate
In the case of passing all the recent three steps correctly, you can run Certbot and fetch your certificates in this section. There are various methods to obtain SSL certificates through plugins by Cerbot. Using the Nginx plugin helps you to reconfigure Nginx and reload the config. Run the command below to use this plugin.
sudo certbot --nginx -d your_domain -d www.your_domainIf you are using certbot for the first time, you will be requested to enter your email address and confirm your acceptance of the terms of service. Following this, certbot will connect to the Let’s Encrypt server and launch a challenge to confirm that you are the owner of the domain for which you are applying for a certificate. If it’s successful, certbot will inquire as to how you want your HTTPS settings to be set up.
Make your selection, then press ENTER . After updating the configuration, Nginx will reload and take the new settings into account. When the procedure is finished, certbot will send you a message informing you of the outcome and the location of your certificates:
You have downloaded, set up, and loaded your certificates. Examine your browser’s security indicator after reloading your webpage with the https:// protocol. It should display a lock icon in the typical green color to show that the website is properly secured.
There is just one step remaining to secure Nginx on Debian 10/11 which is testing the renewal process.
Step 5. Certbot Auto-Renewal Verification
As the latest step, you need to verify Cerbot Auto-Renewal. As we mentioned, Let’s Encrypt’s certificates are only valid for ninety days. So, you have this deadline to automate your certificate renewal process. The certbot package that was installed takes care of this by adding a renewal script to /etc/cron.d . The script runs twice a day and renews any certificate that’s within thirty days of expiration automatically.
Type the command below to test the renewal process:
sudo certbot renew --dry-runThe certbot package also adds a systemd timer that runs twice a day and renews any certificate automatically. To query the status of the timer with systemctl , run:
sudo systemctl status certbot.timerAt this point, Cerbot will renew your certificates and reload Nginx to pick up the changes. Facing no error means you’re all set. If you received an email from Let’s Encrypt warning you when your certificate is about to expire it means the automated renewal process never fails.
Congrats! all the required steps to secure Nginx on Debian are successfully completed.
Conclusion
In this article, you learned How to Secure Nginx on Debian 10/11. You started by installing the Let’s Encrypt client certbot and then SSL certificates were downloaded for your domain, configured Nginx to use these certificates, and set up automatic certificate renewal.
If you followed the required steps of this guide properly, your Nginx must have been secured on your Debian without any errors. However, our technical support team will try their best to solve your problems, if you encounter any problems.