Linux Configuration Files ➞ Complete Explanation and Editing
Without the editing Linux configuration files knowledge, you are not even close to being a perfect Linux administrator. What is happening inside the Linux operating system? Do not worry, this tutorial responds!
Linux configuration files influence the operation of the operating system and are the difference point between Linux and Windows operating systems. Its behavior can be tailored to your requirements thanks to the multitude of configuration files. Linux programs’ configurations are kept in separate configuration files. They are not executable since they are static. Getting familiar with Linux config files is like being in the command center. So, you can change the configuration options or move them to other systems.
While Ubuntu, Debian, CentOS, and other Linux distributions use different Linux configuration files, the naming guidelines are not identical. While these files may have somewhat different names and locations throughout the file system, the overall concept of editing each of these unique configuration files remains the same. Since you most likely make mistakes when editing Linux configuration files, you are highly recommended to make a copy of the configuration file first to protect your preferences and system settings. Also, as a suggestion to recognize it as a backup file, later on, append the .bak suffix to the end of the copy.
After buying Linux VPS, you must know how to manage file permissions and user groups and monitor users and their login state. Linux configuration files are in charge of this responsibility which are usually under the /etc folder and require superuser access. No wonder that they are the reason for the smooth and safe operation of your Linux system.
Join us with this article to learn where configuration files are located and what they do. Also, let’s review the most important configuration files for the most popular Linux distributions. In the end, you will know the essential elements of Linux configuration files, their importance, and pivotal functions inside the Linux environment.
Concept of Linux Configuration Files & Its Importance
Typically, the configuration files are text files that hold the preferences and guidelines for different applications, programs, and procedures. A local Linux file called a configuration (config) file governs the operations of a program, utility, or process. Different parameters and settings for different OS components are contained in the configuration files. These components comprise OS instructions for connecting to internet name servers, user groups, permissions, network access, and protocols. In other words, configuration files are essential components in a Linux system. They give system administrators the ability to alter the OS, manage application and system preferences, and guarantee that the configuration endures during reboots.
In essence, configuration files are fairly basic, but they control incredibly intricate interfaces. Thousands of system features can be found in a single configuration file, which makes them indispensable to a well-operating system. Despite the fact that the majority of distributions provide complex user interfaces (UIs) for system configuration, these UIs only alter system-wide plaintext configuration files. Thus, by comprehending these configuration files, we can become less reliant on these user interfaces and increase our level of Linux expertise.
It is possible to think of the kernel as a “program.” In addition to managing file permissions, the kernel must be aware of the list of users and groups in the system. Programs do not specifically read these files; instead, the kernel uses a function supplied by a system library. The kernel is in charge of this type of function, which is also referred to as a system call.
Rules to Edit Config File in Linux
To modify a Linux configuration file, you simply need to locate it and open it in a text editor. Though you’ll probably be editing these files with a command-line editor like Nano or Vim, many Linux configuration files may be accessed with a plain-text editor and edited directly. For the most part, configuration data in Linux configuration files is stored in plain text; all an administrator needs to do to update the settings is make changes to the file’s contents and save it. Most Linux configuration files are located in a subdirectory of the /etc/ directory.
These configuration files are often modified via the command line. It’s important to remember that these configuration files are usually hidden from regular user accounts, so you may have trouble discovering them if you don’t elevate your privileges before attempting to change them (for example, by using the Sudo or SU command). Even though updated configuration files are saved instantly, apps need to be restarted in order for the changes to take effect.
Types of Linux Configuration Files
System administrators can personalize the operating system, manage application and system preferences, and make sure the configuration lasts through reboots with the help of Linux configuration files. Linux configuration files are separated not just into user-specific and system-wide files, but also based on the type of file. These files are essential for controlling system administration, authentication, and user program behavior configuration.
Two broad categories can be used to classify configuration files:
- System-wide Configuration Files
- As we mentioned earlier, the system is impacted by these configuration files. Usually found in the root (
/) partition, they can only be modified with superuser access. These files are also called Global Config Files. The majority of global configuration files can be found in the/etcdirectory. - The /
etc/ directory contains numerous subdirectories, each containing associated configuration files, and seems more like a filesystem. /etc/X11/, /etc/cups/, /etc/xdg/, /etc/ssh/, /etc/apparmor.d/, and /etc/udev/ are the most useful of these subdirectories.
- User-specific Configuration Files
- These files customize the settings to suit the tastes of each user. They can be modified without requiring superuser permissions and are typically found in the user’s home directory. Global configurations never take precedence over user-specific configurations. Therefore, as long as a user-specific configuration exists, an application will always prefer it. Regarding customizations particular to individual users, our programs adhere to two distinct standards.
- Some of the most commonly used user-specific config files are:
$HOME/.xinitrc,$HOME/.vimrc,$HOME/.bashrc,$XDG_CONFIG_HOME/nvim/init.vim,$HOME/.editor, $HOME/.gitconfig,$HOME/.profile,$HOME/.ssh/config.
Stay with us in this guide to explain the Different Types of Linux Configuration Files and check out the list of the most important configuration files for each type.
Network Access Files
The instructions and guidelines for determining hostnames and managing network access are contained in the network access configuration files. The files set up and oversee host and network service access control policies.
The network domain uses access files to find out how to look for host names. Let’s see what access files are:
- /etc/hosts.config:
Using the/etc/hosts file contains configuration options for hostname resolution. This instructs the network domain server on how to look up host names.
- /etc/hosts
A local database that maps hostnames to IP addresses when DNS is unavailable or for local network configurations.
- /etc/hosts.allow
Establishes guidelines for accepting network services according to standards such as hostnames or IP addresses.
- /etc/hosts.deny
Includes rules that can be used to block network access to particular hosts or services based on hostnames or IP addresses.
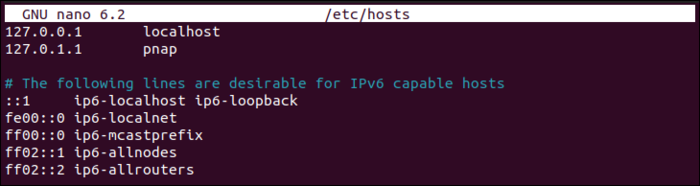
Here is an example of the /etc/hosts file:
Booting and login/logout
The Linux system booting procedure is impacted by the boot configuration files. These files specify system runlevels, control startup services, and supply system information. In order to manage user sessions on a Linux system, login/logout configuration files are necessary. These files provide users with a welcome message and regulate how they log in.
The files that contain configuration information for booting up the system are explained below:
- /etc/issue
A text file that appears before the login prompt and contains system information and a greeting.
- /etc/issue.net
This file is used for network connections and remote logins.
- /etc/rc.d/rc
A script that controls startup services and system runlevels.
- /etc/rc.d/rc.sysinit
A script in charge of mounting filesystems and performing hardware initialization during system boot-up.
- /etc/rc.d/rcX.d/
A directory containing symbolic links to scripts that control services started or stopped at various runlevels.
These files are associated with login/logout:
- /etc/issue
Gives system details and presents a welcome message before the login prompt.
- /etc/issue.net
It is used for network connections and remote logins with the same purposes as /etc/issue.
Files System
The way that file systems and storage devices are mounted and accessed is controlled and specified by file system configuration files. These files aid in defining and controlling storage management settings.
Several crucial files for file system setting are:
- etc/mtab
A file that contains a list of the file systems that are currently mounted together with device, mount point, and file system type details.
- /etc/fstab
A configuration file containing settings specific to each mount point and defining static file system mounts.
- /etc/mtools.conf
Configuration files for tools like mcopy and mdir are specified in the mtools package configuration file, which is used to access and manage MS-DOS (FAT) file systems.
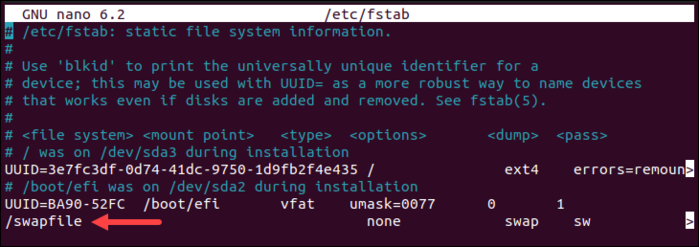
The /etc/fstab file has a line that allows the swap partition to remain active even after reboots, as seen in the image below:
System Administration
System administration is one of the Linux configuration files types that hold important data about user accounts, passwords, groups, file permissions, and system security settings. The integrity and security of the system depend on these files.
Some important administration configuration files are listed below:
- /etc/group
Includes details on user groups, such as names and user accounts connected to the groups.
- /etc/nologin
Stops specific users from logging in which is frequently used to display system maintenance alerts.
- /etc/passwd
keeps track of user account data, such as shell executables, home directories, and user IDs.
- /etc/rpmrc
Global RPM parameters are specified in the RPM package manager‘s configuration file.
- /etc/securetty
lists the terminals (TTYs) that the root user (superuser) can access directly.
- /etc/usertty
lists the terminals that user accounts are permitted to utilize.
- /etc/shadow
Improves password security by storing password hashes and security-related data for user accounts.
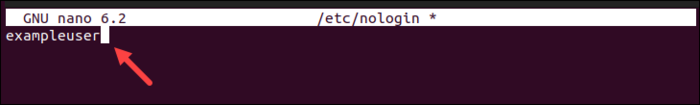
The contents of the /etc/nologin file are seen in the screenshot below, where the exampleuser user is prevented from logging in:
System Commands
System-level utilities and commands needed for system management and operation are detailed in Linux system command configuration files. These files are used to configure and manage system utilities and commands, which guarantees the correct operation of the system’s main parts and functions.
Some important system command configuration files are listed below:
- /etc/lilo.conf
A file that defines how the system should boot and handle different operating systems and is used by the LILO (LInux LOader) bootloader.
- /etc/logrotate.conf
configuration file for the logrotate tool, which sets log rotation policies and maintains log files.
- /etc/identd.conf
Configuration file for the Ident daemon, used by network services such as IRC, that determines the owner of TCP connections.
- /etc/ld.so.conf
A list of folders that the system should look through to find dynamically linked shared libraries for executable files.
- /etc/inittab
System runlevels, actions, and processes to be carried out during system initialization are specified in the configuration file for the init process.
- /etc/termcap
Outlines the features and capabilities of different types of terminals, making it possible for applications to properly communicate with terminal devices.
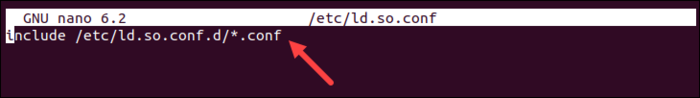
The /etc/ld.so.conf file and the list of folders the system should look through for dynamic links to executable files are shown in the following image:
Daemons
One of the Linux configuration files types is Daemons. These files are essential background programs that carry out specific duties in response to requests from the system, hardware, or network. Daemon configuration files aid in defining their parameters and behavior.
The main daemon configuration files are as follows:
- /etc/syslogd.conf
The syslog daemon (syslogd) configuration file governs the handling and storage of log messages for both system and application logs.
- /etc/httpd.conf
The Apache HTTP server’s (httpd) configuration file specifies the server’s configuration, virtual hosts, and behavior when delivering web content.
Networking
Linux networking configuration files configure and oversee network-related parameters, services, and protocols, guaranteeing dependable and effective network functioning. These files are essential for determining connectivity and network behavior.
The essential networking configuration files are listed in the following order:
- /etc/gated.conf
Gated routing protocol daemon’s configuration file.
- /etc/gated.version
Includes the version number of the gated daemon.
- /etc/gateway
An optional configuration file that provides routing information to the routed daemon.
- /etc/networks
Enumerates network names and addresses that are reachable from your network.
- /etc/protocols
Utilized for network routing via the route command.
- /etc/resolv.con
Lists the network protocols that are currently in use and are utilized for network communication.
- /etc/rpc
Indicates the name server to be contacted in order to resolve IP addresses.
- /etc/exports
Includes guidelines and instructions for using Remote Procedure Calls (RPCs) for NFS calls, mounting remote file systems, and other purposes.
- /etc/services
Permissions and configuration for exporting file systems over NFS.
- /etc/inetd.conf
Translates the names of network services into the port numbers and protocols that different network-related applications employ.
- /etc/sendmail.cf
The inetd configuration file, which manages daemons or services for different network services.
- /etc/sysconfig/network
File used to configure the mail transfer agent sendmail.
- /etc/sysconfig/network-scripts/if*
Red Hat network scripts for interface management in network configuration.
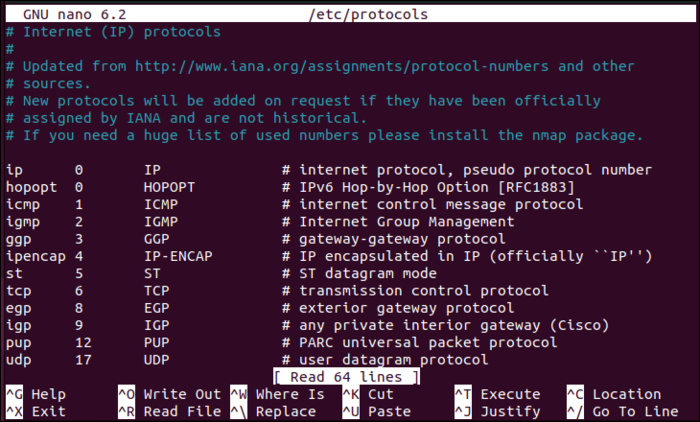
An example of the /etc/protocols file including all the system’s available protocols is as follows:
User Programs
You can personalize and set up apps to your liking using the user program configuration files. Typically, the files are kept in the user’s home directory and are hidden. These hidden files and directories, like config or appname, are prefixed with a. (dot). You can use the ls command to view them. Every time you launch a user or system program, the program reads its configuration files. The config files kept in the /etc/ directory are used to read the default setup. Afterward, the rc and. (dot) files can be used by users to modify the applications.
Final Note:
To prevent permanent system damage, make sure you have a backup and are knowledgeable about the settings before making any changes to any of these files.
Conclusion
In this article, you learned about Linux Configuration Files and editing them. An experienced administrator can set up the Linux kernel and operating system to function in a way that is entirely specific to the current requirements of the network and business. Even though creating certain setups is typically not very difficult, it is still not always simple. We tried to explain the way you can use instructions for editing Linux configuration files.
These configuration files can have a very different syntax because Linux does not impose a standard format for them. However, config files can liberate us from the constraints of user interfaces designed for beginners by using this content and practicing more.